It is almost a cliche, but the femme fatale — the allure of a female spy who gets the lonely male soldier to give up military secrets — is still very much alive and well in the current Syrian civil war. But instead of using actual people, today’s take on Mata Hari has more to do about social networks, phishing, and clever use of a variety of keylogging programs.
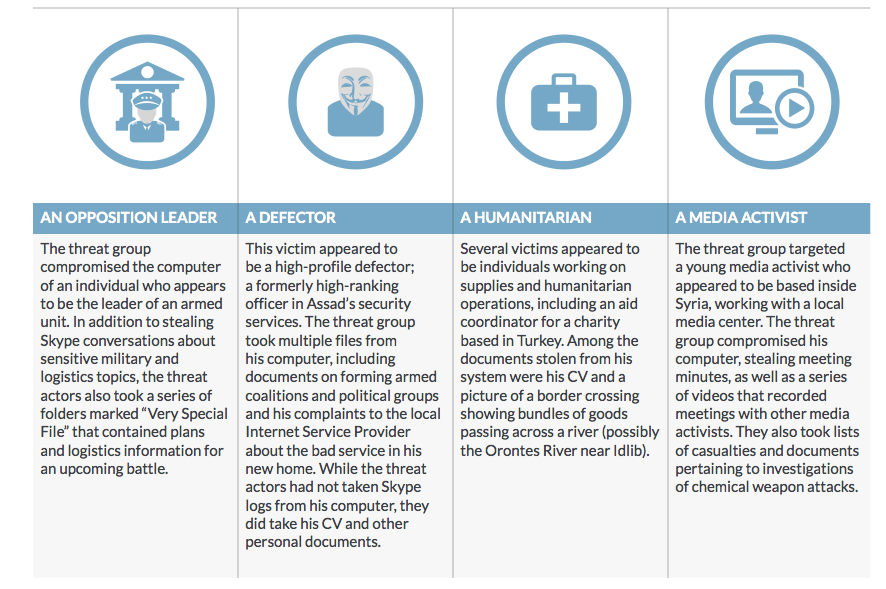
A report this week by FireEye has tracked this trend in Syria and makes for interesting reading. Hackers operated between November 2013 and January 2014 to collect battle plans and specific operational details from the opposition forces’ computers. The information was substantial: FireEye found more than seven GB of data spanning thousands of Skype conversations and 12,000 contact records. So much was taken from the soldiers and insurgents that FireEye was able to assemble profiles of several of them for their report:
What is astounding is how easily the various Syrians fell for some pretty old-fashioned social engineering. Skype contact requests would be sent to the fighters from unknown and seemingly female correspondents. Once they were engaged in text chats, the hackers would ask what kind of computer they were on, and then send them a “better photo” of themselves that, surprise, surprise, turned out to contain malware. Then the data extraction began, and they moved on to others in the target’s contacts.
It isn’t just that loose lips sink ships. It is that lonely guys are so easily manipulated. Back in WWII days, we needed a lot more human infrastructure to collect data to track enemy movements. Nowadays, all it takes is a female avatar and some sympathetic IM patter, a few pieces of code and let the gigabytes roll in.
The hackers were thorough. FireEye found “whole sets of files pertaining to upcoming large-scale military operations. These included correspondence, rosters, annotated satellite images, battle maps, orders of battle, geographic coordinates for attacks, and lists of weapons from a range of fighting groups.” In addition to using the fake female avatars on Facebook and Skype, they also setup a bogus pro-opposition website that would infect visitors with malware. The whole effort was aided by the fact that often soldiers shared computers, so once an infection landed on one PC it could collect multiple identities quite easily.
Finally, the hackers focused on Android phones as well as Windows PCs and had malware created for both environments.
Figuring out who was behind this massive data collection effort isn’t easy, of course. FireEye thinks there are ties to Lebanese or other pro-Syrian groups, and have tracked its command servers to outside of Syria. That could be almost anyone these days. Still, the report is quite chilling in what a determined hacking group can accomplish during wartime.