Chances are, your CEO doesn’t have the best data security hygiene. A recent analysis of passwords leaked by Equifax executives showed they used rather simple passwords that could be easily guessed, let alone made use of multifactor authentication methods. It is time we made our executives more responsible and exemplary users of our corporate security.
After the Equifax breach, researchers found their “chief privacy officer, CIO, VP of PR and VP of Sales, used passwords with all lowercase letters, no special symbols, and easily guessable words like spouses’ names, city names, and even combinations of initials and birth year,” evidence that the company failed to follow best security practices. What makes this worse is the likelihood that numerous internal Equifax apps probably used the identical simple passwords.
While Equifax continues to make news as the security poster child, they aren’t alone and the problem is pervasive. There are hundreds of CEOs of ordinary companies who don’t understand good IT security hygiene. Just because most of these companies haven’t been in the headlines doesn’t mean they aren’t equally poor at their implementations. The 2017 Verizon Data Breach Investigations Report found that a whopping 81% of hacking-related breaches use either stolen or weak passwords. In other words: the breaches came from easily compromised identities.
I have spoken to many IT managers over the years who have told me of their frustration with their top executives when it comes to implementing better security policies. One manager that I interviewed last year (who asks not to be named for obvious reasons) told me that he tried to make a very small change to his organization’s password policy. While he had greater goals, he was trying to deploy a policy that made passwords expire after a certain period. His goal was to try to get ahead of any breaches because many of his users’ passwords to common websites had already been posted in earlier leaks, such as with Yahoo and LinkedIn.
For years his organization had passwords that never expired. He went ahead and got the various management approvals, and was all set to go with this very simple change until he was rebuffed by his CEO. “My CEO told me that he had been using the same password for more than 30 years and wasn’t about to change it now. So we still have hundreds of people using non-expiring passwords around the organization.” Argh.
He isn’t the only frustrated IT manager. And passwords aren’t the only security issue. Another recent study by Code42 found that 75 percent of CEOs and more than half of other top executives admit that they use applications that are not approved by their IT department. This could be caused by a number of factors, including that the security team is not engaged with the C-suite, the executives are just stubborn and clinging to their old ways (such as that 30-year old common password), or that security isn’t taken very seriously by management. Or all three.
But we shouldn’t just blame our executives, when the problem could be our own making. “There will always be a natural tension between the CIO and the CISO,” as Saryu Nayyar wrote in an op/ed in Dark Reading earlier this summer. He is the CEO of Gurucul, a security vendor. “This dynamic is determined by the reality that the CIO is driven to provide more and better services at lower costs, while a CISO’s job is to protect everything.” Over my years with talking to many IT professionals, I have seen lots of such infighting between management teams. Certainly, the time for working together in the name of better security policies has come.
Another reason for CEO security malaise could be that security professionals aren’t good at communicating the actual risks and don’t practice what they preach. What ends up happening is that executives get turned off by the level of effort that is required to lock down their infrastructure. In a recent article in ITWorld, the author talks about how security practitioners are drowning in noise end up taking the hunter mentality and eventually abandon the data itself. “They spot check it and look for very specific patterns that have been successful in the past,” said Bay Dynamics co-founder and CTO Ryan Stolte, interviewed in the article.
So what should CSOs and CISOs do, other than find a more amenable CEO to work for? Start by first assembling some of the horror stories cited above. Look at the root causes of these incidents and try to factor these into your own plans for improving – and simplifying — your enterprise’s security practices.
Understand the value of leaked data and how it can live forever. “I think what’s being overlooked to some extent is the fact that the data that was compromised has perpetual value to a fraudster,” says credit expert John Ulzheimer quoted in this blog post. “In five, 10, 15 years that data will still be valuable to a fraudster.” Certainly that is the case if users stick with their age-old go-to password collections, as has been illustrated here.
Next, you need to be talking about these risks in the only language your CEO understands – money. Security consultant David Froud has written about this extensively. “This is not the language of security, it’s the language of business goals. Or to put it crassly, it’s the language of money,” he said in this post.
Forget about next-generation firewalls, or even last-generation ones. Or the details about how your anti-malware algorithms work. Your CEO isn’t interested. It is all plumbing, and about as exciting. What will get the CEO involved is how much money you can save your company by following a particular practice. Map your organization’s assets to your business processes as a start and make sure you understand how to value each of these processes.
Keep your security as simple as possible, and then people will actually use it. “If the cybersecurity industry was doing its job, it would be SIMPLIFYING things for everyone, not making them worse,’ says Froud in another post. As an example of this, take a closer look at using single sign-on or password manager tools that take the burden of passwords from your users and automate the password creation process. Once you take the creation – and remembering—passwords out of human hands, you have a prayer of fighting back with the criminals who prey on the collections of reused and simple passwords.
There is no point in having a complex multifactor authentication system, for example, if only a portion of the staff uses it. In fact, find a simple multifactor authentication product and get everyone on board. Make sure you implement programs that are workable and usable. Don’t pile on security for security’s sake. And if you are evaluating two different security solutions, choose the simpler one if at all possible. Have I said “simple” enough times here?
Of course, using single sign-on tools isn’t 100 percent secure either. A recent hack into Vevo, an online music video site, was subjected to a phishing attack through LinkedIn that compromised an employee’s Okta account. From this account, the hackers were able to gain access to Vevo’s media servers and helped themselves to terabytes of private files.
That brings up my next point. Any security program should plan on better executive and user awareness education, particularly when it comes to a type of phishing attack called “whaling” or CEO impersonation. These are emails sent by attacks that appear to be coming from your CEO or CFO to transfer huge sums of money, but in reality are just scams writ large. Numerous security vendors offer these programs, if you don’t want to design your own. All it takes is a single email to break through your defenses, as the folks at Vevo found out.
Finally, practice what your preach. If you aren’t trying out what you are going to recommend what everyone is supposed to use, you aren’t going to get very far. Lead by example. Years ago when I first started working in IT, I had a CTO (we didn’t call him that, but that is what he was) who refused to use the Lotus 1-2-3 spreadsheet software that everyone else was getting for their PCs because 1-2-3 came with copy protection on the disk. When he found out that I had a version that removed the copy protection, then he insisted that I install it on his PC. We don’t need more hypocrites in IT. Do as I say and as I do.
Clearly, we still have a long way to go before we can get better-behaving CEOs, at least when it comes to security practice. And maybe convincing them of being able to change their passwords, or heavens, use a password manager or a single sign-on tool. Either could be the first important step.
 Israel is becoming a major center for connected car research. Fueled by government-backed military research, test labs established by automakers and numerous connected car startups, the country has attracted top talent from around the world and provided innovative technologies in automotive cybersecurity.
Israel is becoming a major center for connected car research. Fueled by government-backed military research, test labs established by automakers and numerous connected car startups, the country has attracted top talent from around the world and provided innovative technologies in automotive cybersecurity.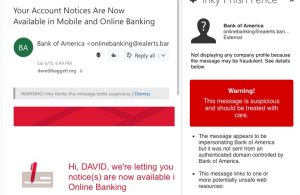
 I haven’t used a bank ATM for years, thanks to the fact that I usually don’t carry cash (and when I need it, my lovely wife normally has some handy). I still remember one time when I was in Canada and stuck my card in one of the cash machines, and was amazed that Canadian money was dispensed. I was amazed at how the machine “knew” what I needed, until I realized that it was only loaded with that currency.
I haven’t used a bank ATM for years, thanks to the fact that I usually don’t carry cash (and when I need it, my lovely wife normally has some handy). I still remember one time when I was in Canada and stuck my card in one of the cash machines, and was amazed that Canadian money was dispensed. I was amazed at how the machine “knew” what I needed, until I realized that it was only loaded with that currency. I spoke to
I spoke to  To provide better spam and phishing protection, a number of ways to improve on email message authentication have been available for years, and are being steadily implemented. However, it is a difficult path to make these methods work. Part of the problem is because there are multiple standards and sadly, you need to understand how these different standards interact and complement each other. Ultimately, you are going to need to deploy all of them.
To provide better spam and phishing protection, a number of ways to improve on email message authentication have been available for years, and are being steadily implemented. However, it is a difficult path to make these methods work. Part of the problem is because there are multiple standards and sadly, you need to understand how these different standards interact and complement each other. Ultimately, you are going to need to deploy all of them. An old scam to separate people from their money has been gaining more popularity. It uses a cellphone protocol called
An old scam to separate people from their money has been gaining more popularity. It uses a cellphone protocol called