Lately, numerous websites have adopted better security practices, supporting a wider variety of multiple factor authentication or MFA. I have been trying these out and for the most part they install relatively easily, although your mileage will vary. The idea is that you want something more than your username (often just your email address) and a password. No matter how complex your password, it can be circumvented by a determined hacker. And many of us (you know who you are) don’t use very complex passwords, or reuse them across various sites.
Let’s start first with the MFA tools that I want to use. First up is Google Authenticator. This is a smartphone app that generates a one-time PIN. You get to the dialog box on your website and enter the PIN and you can complete your login. Google Authenticator is dirt simple to setup: you scan a QR code that is displayed on your screen and it then shows you an entry for your website. The PIN changes every minute, so it is a lot harder to spoof than a code that is sent to your phone via text messaging.
The other tool is the Yubikey, a USB device that supports the FIDO standards from Yubico. There is a small button on the device that you press, and that sends the appropriate code to your website at the appropriate time to complete your login. They are inexpensive and now support a wide variety of website logins. Again, setup is fairly straightforward, and I just leave my key in my desktop’s USB port so I don’t have to worry about losing it.
If you use both methods (and you should, why not), this will prevent someone else from trying to login to your account, even if they know your password. Once you have completed a successful login on one device, you aren’t prompted again for the extra security.
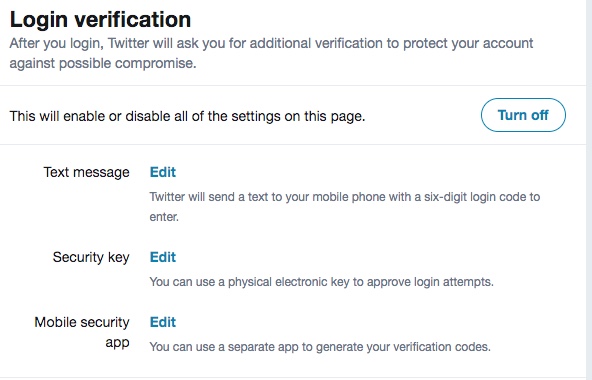
Twitter announced this past week that they support the Yubikey, which adds to their existing support of Google Authenticator and other authenticator apps. Here are the instructions for setting it up. The interface for doing this can be found starting with this menu, under the Security heading. It isn’t all that verbose an interface, but you can choose which of the three methods (text, Yubico key, and mobile app) or all of them to use for the additional security.
Next up is my WordPress blog. If you host your blog on WordPress.org, they have long supported various MFA methods, including Google Authenticator, Authy, Duo and others. If you use WordFence Premium, you can also get the MFA protection. Speaking of WordFence, you really should use it (at least the basic version): it will tell you who is trying to break into your blog and last week I got several thousand attempts, which I think was a new record for me.
So I was more motivated to start having better protection for my login there. Since I use the basic WordFence, I looked around and found miniOrange, another plug-in that supports WordPress as well as Magento, Drupal and Joomla CMS. It works with Google Authenticator as well as its own QR code reader and soft token apps. I used the free version, but if you pay extra for a miniOrange account, you can support more than a single user as well as get additional MFA methods, including Yubikey. There are several other MFA plug-ins for WordPress, but I didn’t try them.
While I was doing these installations, my bitcoin wallet app notified me that they were requiring everyone to add MFA to their logins soon, otherwise I wouldn’t be able to transfer any funds in or out of my account. That is a smart decision, especially given the number of recent exploits in this market space. So I got Google Authenticator working on that as well.
Finally, a few weeks ago I was getting all sorts of notifications that someone was trying to login to my Facebook account, so I wanted to add both Google Authenticator and Yubikey to that login. I ran into problems: when I wanted to add the Authenticator app, Facebook turns on “Allow logins without a code for one week.” You can’t then turn this off without disabling my Authenticator app. I am not sure this is a good idea, but when I went back to check on it for this post I couldn’t find the setting. Your dialog box when done will look like this.
As you can see, this is still not completely ready for your mom’s logins. (At least, it isn’t ready unless you want to support her when she has problems.) But you should take the time and add these tools to protect your own logins.

 The world has changed significantly in the past two years, and so have the rules around assessing cyber security risk. A combination of greater digital business penetration, a wider array of risks, and bigger consequences of cyber threats have made the world of risk management both more complex and more important than ever. Sadly, word hasn’t yet gotten out that risk management is an essential part of today’s business operations. According to this
The world has changed significantly in the past two years, and so have the rules around assessing cyber security risk. A combination of greater digital business penetration, a wider array of risks, and bigger consequences of cyber threats have made the world of risk management both more complex and more important than ever. Sadly, word hasn’t yet gotten out that risk management is an essential part of today’s business operations. According to this 
 Cris Thomas, who also goes by the pseudonym
Cris Thomas, who also goes by the pseudonym 
 There are conflicting reports over whether or not ransomware attacks are growing. Many organizations state (quite convincingly) that it’s the most popular malware form and that ransom-related attacks have been increasing at a rapid rate over the past year. However, other reports offer a more nuanced point of view.While the raw number of ransom-based attacks is increasing, the proportion of ransom-related attacks is dropping over the last part of 2017. Many businesses are not paying out the ransoms, motivating criminals to try other malware methods.
There are conflicting reports over whether or not ransomware attacks are growing. Many organizations state (quite convincingly) that it’s the most popular malware form and that ransom-related attacks have been increasing at a rapid rate over the past year. However, other reports offer a more nuanced point of view.While the raw number of ransom-based attacks is increasing, the proportion of ransom-related attacks is dropping over the last part of 2017. Many businesses are not paying out the ransoms, motivating criminals to try other malware methods. Subject: “We just did a Dark Web search on your three of your anchors, and what we found should scare you and your viewers.”
Subject: “We just did a Dark Web search on your three of your anchors, and what we found should scare you and your viewers.”