 This has been quite a year for data breaches, with reports that numerous unsecured Amazon Web Services storage containers were inadvertently made public, a rise in hidden cryptomining malware, and lots of victims continuing to fall for ransomware and other botnet attacks. So, with that context, let’s look at what security trends 2019 could bring and ways to prepare for the coming year. I cover security awareness training, hiding malware in plain sight with fileless and other techniques, the rise of FIDO2 and better cloud security in my story in HPE’s Enterprise.nxt blog.
This has been quite a year for data breaches, with reports that numerous unsecured Amazon Web Services storage containers were inadvertently made public, a rise in hidden cryptomining malware, and lots of victims continuing to fall for ransomware and other botnet attacks. So, with that context, let’s look at what security trends 2019 could bring and ways to prepare for the coming year. I cover security awareness training, hiding malware in plain sight with fileless and other techniques, the rise of FIDO2 and better cloud security in my story in HPE’s Enterprise.nxt blog.
Category Archives: security
RSA blog: Everyday we should practice cybersecurity awareness
Yes, just like last October, this month we celebrate National Cybersecurity Awareness Month. So let’s look at what happened in the past year since we last honored this manufactured “holiday.”
We started off 2018 with more than three million records breached by Jason’s Deli, moved into spring with five million records from Saks/Lord&Taylor and 37 million care of Panera Bread restaurants. May saw breaches from fitness tracking company PumpUp and clothing retailer UnderArmor. July was a new low point with breaches from Ticketfly, the Sacramento Bee newspaper chain, and MyHeritage. And let’s not forget Exactis with 340 million records placed online.
And there are many, many other companies who have been breached that I haven’t even mentioned. The issue is that with security awareness, you are only as good as yesterday’s response. In this post for RSA’s blog, I have several suggestions on ways to make this month more meaningful and actionable for IT managers.
RSA blog: Everyday we should practice cybersecurity awareness
Yes, just like last October, this month we celebrate National Cybersecurity Awareness Month. So let’s look at what happened in the past year since we last honored this manufactured “holiday.”
We started off 2018 with more than three million records breached by Jason’s Deli, moved into spring with five million records from Saks/Lord&Taylor and 37 million care of Panera Bread restaurants. May saw breaches from fitness tracking company PumpUp and clothing retailer UnderArmor. July was a new low point with breaches from Ticketfly, the Sacramento Bee newspaper chain, and MyHeritage. And let’s not forget Exactis with 340 million records placed online.
Even with this list, I am sure that I haven’t even accounted for many other breaches of the past year, including the various data leaks from GoDaddy, LevelOne Robotics, Nice Systems, Los Angeles’ 211 service center, Localblox, Octoly and Viacom. These and many others put unprotected AWS S3 storage buckets online and forgot to secure them. All it took was a single check box and the data in all of these situations would have been easily secured.
Of course, who doesn’t remember Facebook’s woes, which thanks to Cambridge Analytica divulged more than 100 million of our accounts. And if we look beyond just private data leaks, who could forget the City of Atlanta finding out their backups were worthless after being hit by a ransomware attack. This resulted in the spending millions of dollars, eventually close to their entire annual IT budget to learn that lesson.
With security awareness, you are only as good as yesterday’s response. Every day, someone is trying to leverage their way into your network, your data and your corporate reputation. Every day, your network is being bombarded with thousands of phishing attempts. Someone is sending multiple emails with infected attachments; hackers are continuously trying reused or common passwords, and coming up with new blended threats that we don’t even know how they are constructed. Every day, users are attaching infected phones and laptops to your network that can serve as new entry points for attacks. So do you really want to take a moment and celebrate? Go right ahead. Go have a piece of cake.
But let’s get down to work and make October more meaningful. Let’s use this month to try to do something positive about security awareness that can last more than just a few days and a few meek attempts. It is time to make security awareness a year-round event. And this isn’t just for the IT department, or your security staff, but something that has to happen across the board. Here are a few tips to get started.
Make a goal that this time next year will be the time when all of your users have embraced MFA or FIDO for their business-critical logins. The tools are getting better, FIDO is being supported with more products, and even Facebook and Google and Twitter now support MFA logins. Many of the breaches mentioned above would have not happened, or have had less impact, had accounts been properly secured with multiple authentication factors.
Use this MFA effort as a more complete assessment of your identity and access management strategy. Examine what you are doing here and whether any of the newer technologies – such as adaptive authentication and better risk assessments — can improve your login security.
Learn from Atlanta’s woes and make sure your backups are actually useful. Spend some time ensuring that you can reconstruct your servers in case of anything unfortunate happens from a disk crash to a ransom attack. Not too long ago, I had two hard drive crashes on my equipment in a single week. I didn’t lose any data, thankfully – but I did lose a lot of time in getting both PCs back up and running. And I learned how I can improve my recovery procedures a bit better too. You should conduct regular disaster exercises to see what happens when parts of your network or particular servers are taken offline, and how long it takes you to recover from these events. Everyone can benefit from more resilient operations.Review your cloud storage buckets for unintended data leaks. There are numerous security tools (if we can mention RiskIQ’s CloudGoat) that can help you assess your storage buckets and ensure that they are properly protected and not sitting ducks online.
Do continuous user awareness training. There are many vendors that can help with putting together a program. The trick is not doing so just once a year, but on a continuous basis. Think about how you can offer incentives to your users, not just make the training onerous and thereby ineffective. One vendor offers a program that performs assessment, education, reinforcement, and measurement in a continuous cycle.
Go back to security school. Folks like SANS offer plenty of training for security staff to brush up on their techniques and tools. We all need refreshers to stay current with what the bad guys are constantly cooking up.
It’s time we realized that security awareness needs to be a year-long focus and not just one-and-done.
Security Intelligence blog: Is Your Site Protected Against Drupal Security Flaws?
 Drupal is a leading open source content management tool that hosts a significant portion of the most popular websites on the internet. If you have not heard about the Drupal security flaws from earlier this year, then you need to take a closer look at what happened and start taking precautions to protect your own installations. You can read my post in IBM’s Security Intelligence blog here.
Drupal is a leading open source content management tool that hosts a significant portion of the most popular websites on the internet. If you have not heard about the Drupal security flaws from earlier this year, then you need to take a closer look at what happened and start taking precautions to protect your own installations. You can read my post in IBM’s Security Intelligence blog here.
CSOonline: Lessons learned from the Park Jin Hyok indictment
 Last month the US DoJ unsealed this indictment of a North Korean spy Park Jin Hyok that they claim was behind the hacks against Sony and the creation and distribution of Wanna Cry. It is a 170+ page document that was written by Nathan Shields of the FBI’s LA office and shows the careful sequence of forensic analysis they used to figure out how various attacks were conducted. In this post for CSOonline, I talk about some of the implications for IT managers, based on the extensive details described in the indictment.
Last month the US DoJ unsealed this indictment of a North Korean spy Park Jin Hyok that they claim was behind the hacks against Sony and the creation and distribution of Wanna Cry. It is a 170+ page document that was written by Nathan Shields of the FBI’s LA office and shows the careful sequence of forensic analysis they used to figure out how various attacks were conducted. In this post for CSOonline, I talk about some of the implications for IT managers, based on the extensive details described in the indictment.
The legalities of hacking back (presentation)
There is a growing trend in information security to be able to hack back or use various direct measures to attack your attackers. There are several issues:
- attributing an attack to the right source,
- understanding the attacker’s intent, and
- developing the right red team skills.
In this talk given at Secure World St. Louis this month, I will talk about the ways that an enterprise can defend itself, and how to go about this process.
How Tachyon brings a fresh perspective on keeping your endpoints healthy
If you run the IT security for your organization, you probably are feeling two things these days. First, you might be familiar with the term “box fatigue,” meaning that you have become tired of purchasing separate products for detecting intrusions, running firewalls, and screening endpoints for malware infections. Secondly, you are probably more paranoid too, as the number of data breaches continues unabated, despite all these disparate tools to try to keep attackers at bay.
I spent some time last month with the folks behind the Tachyon endpoint management product. The vendor is 1E, which isn’t a name that you often see in the press. They are based in London with a NYC office, and have several large American corporations as customers. While they paid me to consult with them, I came away from my contact with their product genuinely impressed with their approach, which I will try to describe here.
A lot of infosec products try to push the metaphor of searching for a needle (such as malware) in a haystack (your network). That notion is somewhat outdated, especially as malware authors are getting better at hiding their infections in plain sight, reusing common code that is part of the Windows OS or chaining together what seems like innocuous routines into a very destructive package. These blended threats, as they are known, are very hard to detect, and often live inside your network for days or even months, eluding most security scanners. This is one of the reasons why the number of breaches continues to make news.
What Tachyon does isn’t trying to find that needle, but instead figures out that first you need to look for something that doesn’t appear to be a piece of hay. That is an important distinction. In the memorable words of Donald Rumsfeld, there are unknown unknowns that you can’t necessary anticipate. He was talking about the fog of war, which is a good analogy to tracking down malware.
 The idea behind Tachyon is to help you discover all sorts of ad hoc and serendipitous things out of your collection of computers and networks that you may not even have known required fixing. Often, issues that start out with some security problem end up becoming general IT operations related when they need to be fixed. Tachyon can help bridge that gap.
The idea behind Tachyon is to help you discover all sorts of ad hoc and serendipitous things out of your collection of computers and networks that you may not even have known required fixing. Often, issues that start out with some security problem end up becoming general IT operations related when they need to be fixed. Tachyon can help bridge that gap.
Today’s enterprise has an increasingly more complex infrastructure. As companies move to more virtual and cloud-based servers and more agile development, there are more moving parts that can be very brittle. Some cloud-based businesses have hundreds of thousands of servers running: if just a small fraction of a percent of that gear has a bug, it becomes almost impossible to ferret out and fix. This post on LinkedIn’s engineering blog is a good case in point. “Any service that is live 24/7 is in a state of change 24/7, and with change comes failures, escalations, and maybe even sleepless nights spent firefighting.” And that is just dealing with production systems, rather than any deliberate infections.
Unlike more narrowly-focused endpoint security products, Tachyon operates in a wider arena that responds to a lot of different events that deal with the entire spectrum of IT operations– not just related to your security posture. Does it matter if you have been infected with malware or have a problem because of an honest mistake by someone with setting up their machine? Not really: your environment isn’t up to par in either situation.
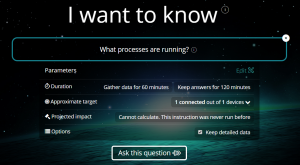
So how does Tachyon do this? It is actually quite simple to explain, and let me show you their home screen:
Does that query box at the top remind you of something? Think about Tachyon as what Google was trying to do back in the late 1990s. Back then, no one knew about search engines. But we quickly figured out that its simple query interface was more than an affectation when we got some real utility out of those queries. That is where we are today with Tachyon: think of it as the search tool for finding out the health of your network. You can ask it a question, and it will tell you what is happening.
Many security products require specialized operators that need training to navigate their numerous menus and interpret their results. What Tachyon is trying to do is to use this question-and-answer rubric that can be used by almost anyone, even a line manager, to figure out what is ailing your network.
But having a plain Jane home page is just one element of the product. The second important difference with Tachyon is how it automates finding and updating that peculiar piece of hay in the stack. I won’t get into the details here, but Tachyon isn’t the only tool in the box that has automation. While there are many products that claim to be able to automate routine IT functions, they still require a lot of manual intervention. Tachyon takes its automation seriously, and puts in place the appropriate infrastructure so it can automate the non-routine as well, to make it easier for IT staffs to do more with fewer resources. Given the reduced headcounts in IT, this couldn’t come at a better time.
If you would like to learn more about Tachyon and read the full review that I wrote about the product, download the PDF here and you’ll see why I think highly of it. And here is a short video about my thoughts on the product.
Now I realize that having 1E as a client could bias my thinking. But I think they are on to something worthwhile here. if you are looking for way to respond and resolve network and endpoint problems at scale, they deserve a closer look.
CSOonline: New ways to protect your AWS infrastructure
 Properly testing your virtual infrastructure has been an issue almost since there were virtual VMs and AWS. Lately, the tool sets have gotten better. Part of the problem is that to adequately test your AWS installation, you need to know a lot about how it is constructed. CPUs can come and go, and storage blocks are created and destroyed in a blink of an eye. And as the number of AWS S3 data leaks rises, there have to better ways to protect things. Rhino Security and Amazon both offer tools to improve visibility into your AWS cloud environments, making it easier to find configuration errors and vulnerabilities.I write about Pacu and CloudGoat tools as well as various AWS services to test your VMs in my article from CSOonline here.
Properly testing your virtual infrastructure has been an issue almost since there were virtual VMs and AWS. Lately, the tool sets have gotten better. Part of the problem is that to adequately test your AWS installation, you need to know a lot about how it is constructed. CPUs can come and go, and storage blocks are created and destroyed in a blink of an eye. And as the number of AWS S3 data leaks rises, there have to better ways to protect things. Rhino Security and Amazon both offer tools to improve visibility into your AWS cloud environments, making it easier to find configuration errors and vulnerabilities.I write about Pacu and CloudGoat tools as well as various AWS services to test your VMs in my article from CSOonline here.
My visit to Bletchley Park and Colossus
I have been a fan of the WWII effort to build special-purpose machines to break German codes for many yea rs, and last wrote about Colossus here, the two-room sized digital computer that was the precursor to the modern PC era. I first found out about this remarkable machine and the effort behind it with a 2007 book that you can still purchase from Amazon.
rs, and last wrote about Colossus here, the two-room sized digital computer that was the precursor to the modern PC era. I first found out about this remarkable machine and the effort behind it with a 2007 book that you can still purchase from Amazon.
But there is no substitute for actually visiting the hallowed ground where this all happened, which I finally did last weekend when I was in London on a consulting assignment. I was fortunate that I had a colleague (and avid reader) who lived nearby and was willing to take me around: he hadn’t been there in a while. I have included some photos that I took during my day at Bletchley Park, and it was great to finally see Colossus in all of its mechanical glory. As you can see from this photo, it looks more like an attic of used spare parts but I can assure it is quite a special place.
 When most people think of decrypting codes, they think a “Matrix” style special effect where gibberish is turned into readable text (German in this instance). Or when you open a file and hit a button that will automatically decrypt the message. This is far from what happened in the 1940s. Back then, it was a herculean effort that involved recoding Morse code radio signals, transferring them to paper tape, using various cribs and cheat sheets to guess at the codes, and then processing the paper tapes through Colossus. What we also don’t realize is that these two rooms full of gear were built without anyone actually seeing the actual German Lorentz coding machine that was used to encrypt the messages to begin with. (The Bombe, a much simpler device, was used to decrypt Enigma codes.) It looks like a very strange machine, but obviously something that was designed to be carted around in the field to send and receive messages.
When most people think of decrypting codes, they think a “Matrix” style special effect where gibberish is turned into readable text (German in this instance). Or when you open a file and hit a button that will automatically decrypt the message. This is far from what happened in the 1940s. Back then, it was a herculean effort that involved recoding Morse code radio signals, transferring them to paper tape, using various cribs and cheat sheets to guess at the codes, and then processing the paper tapes through Colossus. What we also don’t realize is that these two rooms full of gear were built without anyone actually seeing the actual German Lorentz coding machine that was used to encrypt the messages to begin with. (The Bombe, a much simpler device, was used to decrypt Enigma codes.) It looks like a very strange machine, but obviously something that was designed to be carted around in the field to send and receive messages.

Sadly, the reconstructed computer is not doing very well. This is no surprise, given that it is made of thousands of vacuum tubes (what the Brits call valves, which evokes an entire Steam Punk ethos). Only a few segments of the process that was used for the decrypts could be demonstrated, and it seems a collection of volunteer minders is kept very busy at keeping the thing in some working order. Here you can see an illustration of what it took to use the Bombe machines, which were more mechanical and didn’t involve true digital computing.

If you decide to visit Colossus, you will need to go to two separate places that are only a short walk apart. The first is the Bletchley Park estate itself, where there are several outbuildings that contain curated exhibits about the wartime effort, including several tributes to the some of the thousands of men and women that worked there during the war. One of the more notorious was Alan Turing, and you can see a mock up of his office here. After the movie The Imitation Game came out, his popularity rose and the park was quite crowded, albeit it was a holiday weekend. There are copies of some of his mathematic al papers (shown below), a brick wall that honors many of the park’s contributors, and the formal apology letter from the British government that cleared his name. Turing’s 1950 paper was one of the seminal works in the history of digital computing and was also shown in one of the exhibits. What I found fascinating was how much of this stuff was being soaked up by the ordinary folks that were wandering around the park. I mean, I am a geek but there were school kids that were absorbed in all of this stuff.
al papers (shown below), a brick wall that honors many of the park’s contributors, and the formal apology letter from the British government that cleared his name. Turing’s 1950 paper was one of the seminal works in the history of digital computing and was also shown in one of the exhibits. What I found fascinating was how much of this stuff was being soaked up by the ordinary folks that were wandering around the park. I mean, I am a geek but there were school kids that were absorbed in all of this stuff.

One of the lesser-known individuals that was honored at the park was a double agent that was known by Garbo, because he was such an impressive actor. I read this book not too long ago about his exploits, and he played key roles in the war effort that had nothing to do with computers. He invented entire networks of imaginary spies when he filed his reports with the Germans that were so convincing that they moved their troops before D-Day, thus saving countless Allied lives.
But the entry to the park doesn’t get you to the reconstructed Colossus, and for that you have to walk down the road and pay another fee to gain access to the British computer history museum. It has numerous other exhibits of dusty old gear, including the first magnetic disks that held a whopping 250 MB 2 MB of data (I think it was mislabeled) and were the size of a small appliance. It was interesting, although not as much fun nor as comprehensive as the museum in San Jose, California. I hope you get a chance to visit both of the Bletchley places and see for yourself how computing history was made.
Internet Protocol Journal: Understanding fileless malware
I have written for this excellent 20 year-old publication occasionally. My article in this issue is about fileless malware.
 Malware authors have gotten more clever and sneaky over time to make their code more difficult to detect and prevent. One of the more worrying recent developments
Malware authors have gotten more clever and sneaky over time to make their code more difficult to detect and prevent. One of the more worrying recent developments
goes under the name “fileless.” There is reason to worry because these kinds of attacks can do more damage and the malware can persist on your computers and networks for weeks or months until they are finally neutralized. Let’s talk about what this malware is and how to understand it better so we can try to stop it from entering our
networks to begin with. Usually, the goal of most malware is to leave something behind on one of your endpoints: one or more files that contain an executable program that can damage your computer, corral your PC as part of a botnet, or make copies of sensitive data and move them to an external repository. Over the years, various detection products have gotten better at finding these residues, as they are called, and blocking them.
You can read my article here, along with other fine pieces on the state of the Internet in this month’s edition.