Last month, I wrote about the evolution of Instant Messaging interoperability. Since posting that article, the users of WhatsApp have fled. The company (which has been a subsidiary of Facebook for several years now) gave its users an ultimatum: accept new business data sharing terms or delete their accounts. For some of its billion global users, this was not received well, especially since some of your data would be shared across all of Facebook’s other operations and products. The change was indicated through a pop-up message that requires users to agree to the changes before February 8. The aftermath was swift: tens of millions of users signed up for either Signal or Telegram within hours of the news.
If you are interested in getting more of the details and my thoughts about whether to stay with WhatsApp or switch to Telegram or Signal, you should take a gander over on the Avast blog and read my post.
WhatsApp pushed off the change until May, which was probably wise. There was a lot of bad information about what private data is and isn’t collected by the app and how it is shared with the Facebook mothership. For example: while the change deals with how individuals interact with businesses, Facebook has and will continue to share a lot of your contact data amongst its many properties. What this whole debacle indicates though is how little most of us that use these IM apps every day really understand about how they work and what they share. My Avast blog tracks down the particular data elements in a handy hyperlinked reference chart.
The problem is that to be useful your IM app needs to know your social graph. But some apps — such as Signal — don’t have to know much more than your friends’ phone numbers. Others — such as Facebook Messenger — want to burrow themselves into your digital life. I found this out a few years ago when I got my data dump from Facebook, and that was when I deleted the standalone smartphone app. I still use Messenger from my web browser, which is a poor compromise I know.
Speaking of downloading data, I requested my data privacy report from WhatsApp and a few days later got access. There are a lot of details about specific items, such as my last known IP address, the type of phone I use, a profile picture, and various privacy settings, This report doesn’t include any copies of your IM message content, and was designed to meet the EU GDPR requirements. I would recommend you request and download your own report.
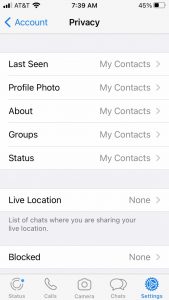 One of the sources that I found doing the research for my blog post was from Consumer Reports that walked me through the process to make WhatsApp more private. You can see the appropriate screen here. Before today, these items were set to “everyone” rather than “my contacts” — there is a third option that turns them off completely. This screen is someplace that I never visited before, despite using WhatsApp for years. It shows you that we have to be vigilant always about our privacy — especially when Facebook is running things — and that there are no simple, single answers.
One of the sources that I found doing the research for my blog post was from Consumer Reports that walked me through the process to make WhatsApp more private. You can see the appropriate screen here. Before today, these items were set to “everyone” rather than “my contacts” — there is a third option that turns them off completely. This screen is someplace that I never visited before, despite using WhatsApp for years. It shows you that we have to be vigilant always about our privacy — especially when Facebook is running things — and that there are no simple, single answers.
Never before have we so many choices when it comes to communicating: IM, PSTN, IP telephony and web conferencing. We have shrunk the globe and made it easier to connect pretty much with anywhere and anyone. But the cost is dear: we have made our data accessible to tech companies to use and abuse as they wish.
 A novel experiment in deploying large-scale trusted data networks has begun in Helsinki, the capital of Finland. A variety of city services have been linked together using the open-source MyData Global solution, it was announced earlier this month. This puts city at the forefront of how it gathers data from its citizens and how it stores and uses the data. The goal is to give each person control over how their data is shared with various city agencies.
A novel experiment in deploying large-scale trusted data networks has begun in Helsinki, the capital of Finland. A variety of city services have been linked together using the open-source MyData Global solution, it was announced earlier this month. This puts city at the forefront of how it gathers data from its citizens and how it stores and uses the data. The goal is to give each person control over how their data is shared with various city agencies. The FDA has appointed Kevin Fu its first Acting Director of Medical Device Cybersecurity in the Center for Devices and Radiological Health. This center has several bodies, including the CyberMed Safety Board, the
The FDA has appointed Kevin Fu its first Acting Director of Medical Device Cybersecurity in the Center for Devices and Radiological Health. This center has several bodies, including the CyberMed Safety Board, the  Sandbox security is complementary to honeypots. It usually involves a special VM that is kept in isolation from the rest of your network resources. Its sole purpose is to be a miniature laboratory to observe malware behavior. Security researchers have been using such sandboxes to analyze malware for many years. Because the sandbox is a controlled environment, its code can be dissected line by line without worrying about potential harm to other computers.
Sandbox security is complementary to honeypots. It usually involves a special VM that is kept in isolation from the rest of your network resources. Its sole purpose is to be a miniature laboratory to observe malware behavior. Security researchers have been using such sandboxes to analyze malware for many years. Because the sandbox is a controlled environment, its code can be dissected line by line without worrying about potential harm to other computers.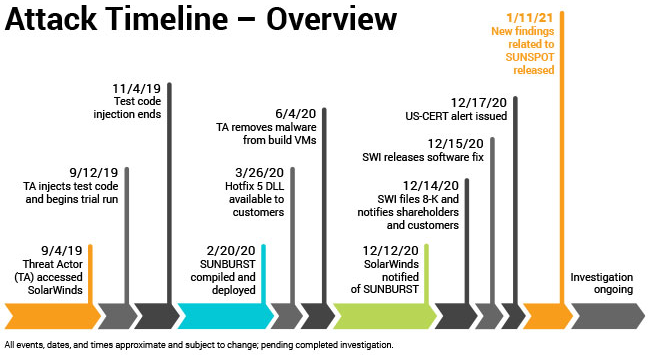

 You might have missed the news about a
You might have missed the news about a  One of the most popular attack methods in IT security starts with posing a simple question: How many places in your IT infrastructure have administrative access? Unfortunately, getting to the bottom of answering this question is anything but simple, but it can be instructive. This is because understanding administrative access is perhaps one of the most important ways to defend your business computing network.
One of the most popular attack methods in IT security starts with posing a simple question: How many places in your IT infrastructure have administrative access? Unfortunately, getting to the bottom of answering this question is anything but simple, but it can be instructive. This is because understanding administrative access is perhaps one of the most important ways to defend your business computing network.