A well-known security tool, SecurityHeaders.com, is now part of many services that Probely offers. The company has a full range of web application and API vulnerability scanning solutions. That news story hides the history and importance of the union and its principal, Scott Helme. I had an opportunity to talk to him directly and find out what led to the change.
For those of you that aren’t familiar with Security Headers, it is a free website that can test your own site for weaknesses in various HTTP protocol and web policy implementations. Helme launched the site in 2015 after an experience testing his own home broadband router that could result in a compromised network. “I was just a guy with a hobby doing security research,” he told me recently. That led to a series of well-publicized other hacks, such as on the computers onboard the Nissan Leaf cars that he investigated with Troy Hunt. He also did some live hacks on TV of audience members’ equipment.
Since it was launched, the site has done 250M website scans.
Helme has worked with Probely since the company became a sponsor two years ago. “By joining forces with Probely, I’m incredibly happy that Security Headers will remain stable and viable for years to come!” said Helme. The union was designed for the site to be more sustainable and to leverage more resources, since until now it has been solely his own labors.
Helme’s goal with Security Headers was to make information security more comprehensible and actionable for the average person. That is why the site, and other tools that he offers, are all free and open. That will continue under the new regime at Probely. “I’ve put so much thought into it, working with these people, what they do, how they do it, and how they align with what I do,” he said. “We have a lot in common.”
So I decided to try it out for myself, and I was quite surprised. I have had a website for almost 30 years, and while I knew about the Security Headers site never actually did a scan. Here are my results:
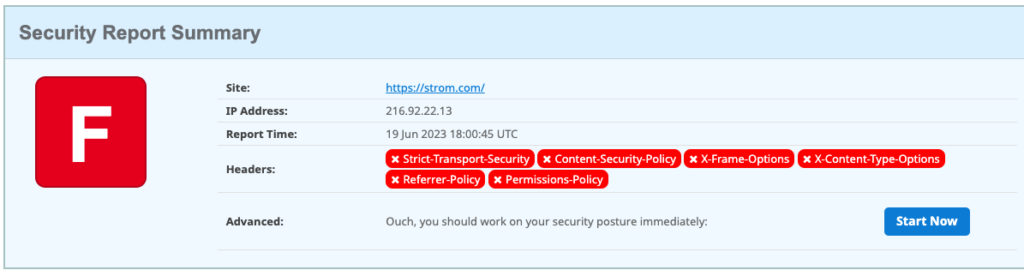
Pretty miserable, right? I basically failed every one of Helme’s six tests. But I was in good (or bad) company: about half of those 250M scans also resulted in an “F” grade.
So — I have a lot of work to do. The results page doesn’t just show the failures, but also provides links to content from Helme on how to learn more about these protocols and policies and what I need to do to fix them to get a better grade — and improve my site’s security. For example, the page links to improvements in hardening my response headers, doing a better job of defining my content security policies and implementing strict transport security protocols. The content is based on numerous talks that Helme has given (and will continue to give) over the years and is written clearly with copious code examples too.
But here is my dirty not-so-secret: I have zero experience with setting up website header parameters. This is probably the reason why my site received a failing grade. After years — decades — of experience setting up various web servers, I have never touched the header configurations of any of my servers. Back in the early days of the web, these parameters didn’t exist. So I can cut myself a little slack. But really, I should have known better, after all the stuff that I write about infosec down through the years. But that is one of the reasons why I try to be as hands-on as I can, and now I have some work to do and things to learn.
That is the essence of what he and Probely are trying to do — to teach us all how to have more secure sites.