 The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post reported yesterday. My story for SiliconANGLE here.
The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post reported yesterday. My story for SiliconANGLE here.
Category Archives: Published work
SiliconANGLE: The summer of adversarial chatbots
This has been the summer of adversarial chatbots.
Researchers from SlashNext Inc. and Netenrich discovered two such efforts, named WormGPT and FraudGPT. These cyberattack weapons are certainly just the beginning in a long line of products that will be developed for nefarious purposes such as creating very targeted phishing emails and new hacking tools. This summer demonstrated that generative artificial intelligence is quickly moving into both offensive and defensive positions, with many security providers calling out how they are using AI methods to augment their defensive tools. The AI security arms race has begun.
You can read my post in SiliconANGLE here.
SiliconANGLE: How Kremlin-backed social media campaigns continue to spread disinformation
A new report sponsored by the European Commission has found that social media has played a key role in the spread of Russian-backed disinformation campaigns since their war with Ukraine began.
“Over the course of 2022, the audience and reach of Kremlin-aligned social media accounts increased substantially all over Europe,” the researchers stated in the report, “Digital Services Act: Application of the Risk Management Framework to Russian disinformation campaigns.”
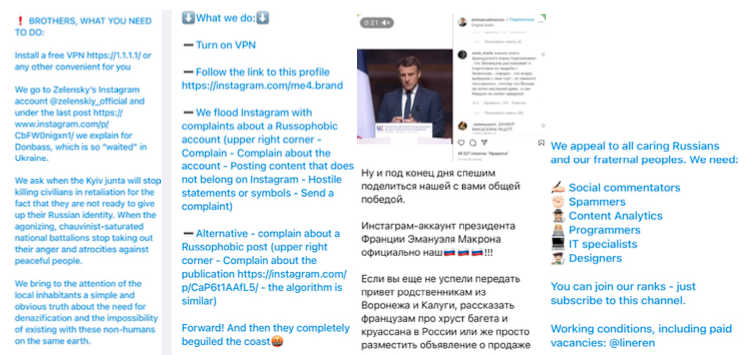
Here you can see various recruitment lures to join Russia’s cyber army who call themselves “Cyber Front Z” and are looking for help on Telegram to post content across networks, up- and down-vote posts, and hound opponents with derogatory comments. The photo shown in the screenshot above is one such target, a pro-Ukraine politician.
The work was done by the nonprofit group Reset and published last week. The group examined these campaigns across 10 languages and over a year. It can serve as useful guidance for U.S. regulators and for how businesses should moderate their own social media content. You can read my analysis for SiliconANGLE here.
SiliconANGLE: News of the week
- Microsoft revokes the certificates that were once VeriSign’s, now owned by DigiCert. Lots of confusion ensues.
- Lazarus Group strikes again, this time leveraging open source frameworks and more lethal tools. This criminal group — an arm of the North Korean government — has been active for years spreading all sorts of trouble via ransomware and other attacks.
- Pam Baker’s new book, ChatGPT for Dummies, is useful in a variety of situations, even if you think you already know a lot about the service and AI.
- The life and hard times of phishing-as-a-service malware groups, how they ply their criminal trade and how they work.
SIliconANGLE: Meta’s Facebook finally supports end-to-end message encryption
The importance of end-to-end encryption of digital messages is getting new attention with the announcement that Meta Platforms Inc.’s Facebook will partly add the feature to its Messenger product now, and eventually for all use cases such as group chats by year-end.
It’s an important step, since E2EE, as it’s known for short, is a critical method of providing secure communication that keeps outside parties from accessing data while it’s transferred between systems or devices. But the announcement isn’t the whole story, either, because Facebook is playing catch-up with many of its competitors, such as Signal and Telegram, which have offered E2EE messaging products for years now.
SiliconANGLE: How the new breed of business VPNs will keep them relevant in security
Since virtual private networks were invented nearly 30 years ago as a way to extend a corporate network across the work, they’ve gone through a complete role reversal, even as they’ve continued to evolve to help protect business users’ data and communications. Today’s VPN is now the linchpin for a series of edge business security technologies, taking center stage thanks to a few trends: the popularity of hybrid working conditions brought on by the COVID pandemic, the movement to the cloud away from on-premises servers, and the acceptance of software-as-a-service tools that made it easier to deploy and manage these clouds.
Evaluating password managers, again
There are two things you need to know about me, if you haven’t already caught on reading my screeds all this time:
- I am very concerned about my infosec, to the point where I continuously evaluate new ways to protect myself. This means I go down a lot of rabbit holes and kiss a lot of frogs. Or whatever trite phrase you’d like.
- I am extremely cheap when it comes to adding monthly subscriptions to do the above. Thus, I tend to be more interested in the free tiers, and carefully weigh the pros and cons of bumping up to something more expensive.
So let’s talk about the basket of services that include a password manager, an encrypted email provider, and an email alias provider. Before a few weeks ago, this looked like the following:
Zoho Vault – This is entirely free, and is an excellent password manager, works across desktops, mobiles and browsers. For some reason, this app isn’t on many people’s radar, which is a shame because I like the other Zoho apps too and think they are a standup company. I switched over to Zoho after getting tired dealing with all the Lastpass breaches. Importing (from Lastpass) and exporting my password collection is simple, with one caveat that I will get to in a moment.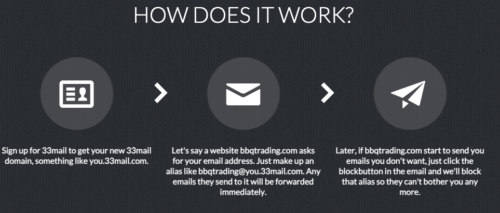
33mail.com – for mail aliases. I have the free Lite version, which has a 10MB bandwidth limits on how much email they will forward to you. I have hit that a few times, and their cheapest paid pricing tier is $1/month. It is easy to create an alias (you just type it into the website’s subscription form that you want to use) and your emails now come filtered through their service. Why would you want to use this service? If you don’t like giving out your “real” email address, this adds an extra layer of control and you can quickly turn off the flood of messages.
ProtonVPN. I have been using the free version with a few minor issues, mostly when I travel or take up residency in some coffee shop. Unlike Brian Chen, I don’t want to build my own VPN (I just don’t trust myself). Speaking of VPNs, I wrote a piece for SiliconANGLE which takes a look back at the history of VPNs, and how they have changed roles, ironically thanks to the pandemic and the way we now work most remotely. .
ProtonVPN just came out with a new pricing scheme and a new password manager app, and so in the interests of the First Directive, I wanted to try them out. Thanks to my friendly PR person, who gave me a press upgrade to their unlimited plan. This is $10/month if you buy a year-long package. This includes several of their services, including encrypted email and their password manager. The VPN on its own is $6/month.
My tl;dr is that the Proton password manager is still too early to rely on, and I am back to using Zoho Vault in production. My reasons:
- Importing my password collection from Zoho to Proton was a nightmare that took a series of false starts and several emails to resolve my issues. Yes, they have some imports that have been put up, but not Zoho’s. I had to create a CSV and use Excel to edit the collection. Yuck.
- It doesn’t have a lot of features, as witnessed by this roadmap of what is to come. Not having a desktop app means if you are trying to enter a password outside of your browser, you will have some effort involved.
I still like Proton as a company: they care about their users’ privacy and security and try to be as transparent as possible, as that roadmap post shows.
Department of Self-promotions
Speaking of SiliconANGLE, I wrote a bunch of stories this week that you might be interested in reading, including about new Google Workspace security features, Proton’s VPN service, and trends in malvertising.
SiliconANGLE news of the week
News items that I wrote this week include:
- Google adds new security features to its Workspace. The features cover aspects of implementing zero-trust security, data loss prevention or DLP, and data privacy controls. Many involve a series of automated improvements that will continuously monitor data placed in Google Drive, using its AI engine.
2. Proton adds new business-oriented VPN packaging to its services. The features build upon existing adware blockers, a smart protocol called Stealth that automatically chooses the best-performing connection, and support for both WireGuard and OpenVPN protocols.
3. Malvertising trends: The malware exploits known as malware-infected ads, or malvertising, have been around for decades, but new reports point to a steady rise in lethality. The technique continues to be profitable, because the malware ads are masquerading as normal ads in the ad networks and using the network as a distribution and funds collection system.:
SiliconANGLE: Doing business in Europe? Time to focus on its new Digital Services Act – now
The European Commission enacted its Digital Services Act last November as another step in its efforts to regulate online services and platforms. Most of these regulations take effect next February, but some will require many European businesses — and others that have customers on the continent — to meet the first deadlines next week. Once again, Europe is moving further ahead of the U.S. in terms of privacy protection and forcing online businesses to be more transparent. This began with the General Data Protection Regulation five years ago and continues with the implementation of the DSA. More about this set of new regs in my latest post for SiliconANGLE here.
SiliconANGLE news: Preventing MFA Fatigue, New IoT compromise attacks
Two new analysis blogs for SiliconANGLE this week:
- Preventing MFA Fatigue.There is a new wave of infections spreading throughout the world that has nothing to do with COVID or, for that matter, any other physical disease. Called multifactor authentication fatigue, it’s highly contagious and spreads through the deception of determined hackers who want to steal users’ account details. But here is the irony: The more MFA a company uses, the greater the chance that a potential MFA fatigue attack will succeed.
- Codesys IoT vulnerability discoveredMicrosoft security researcher Vladimir Tokarev demonstrated an interesting attack on the industrial internet of things automation software called Codesys. Tokarev, who showed the exploit last week at the annual BlackHat security conference in Las Vegas, used a miniature elevator model to demonstrate how the attack could crash its cab. The software – and more importantly, its software development kit — is widely used in millions of programmable logic controller or PLC chips that run everything from traffic lights and water treatment plants to commercial building operations automation and energy pipelines.