We are in love with our mobile devices – especially those of us who rely on them at work. They keep us connected, informed, and with a smart mobile strategy in place, they enable us to work efficiently at the highest possible productivity level.
Companies, in turn, are aware of the demands created by mobilizing employees. Gone are the days where IT controlled the endpoint computing device. Today’s users expect IT to support their device choices and to help them thrive in a rapidly changing mobile environment. But with freedom of choice comes consequences. IT must prepare for better mobile management and security measures, building custom apps, deploying and supporting a range of devices, and transitioning from the task of selecting hardware to becoming a mobile systems integrator.
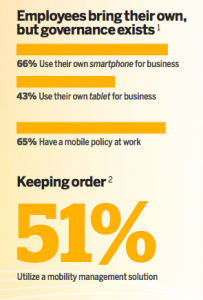
Momentum around mobile in the enterprise plays out in the numbers. 81% of companies surveyed by IDG have mapped out a mobile strategy, 47% have deployed mobile apps beyond email, but for most, security lags behind – only 7% say they are secured across all areas. (See chart for survey details). Links TK
While the mobile end game is different for every company, the ultimate destination for some businesses is to convert aging desktops into a 100% mobile-only population, where users can approach a level of productivity that they previously had with their Windows and Mac desktop applications. Some have already made that transition. For others, it can be years away.
Part of the challenge is how mission-critical enterprise applications translate to devices. Do they offer a viable mobile experience? Some corporations are making sure they do. The percentage of companies that wrote internal apps for mobile devices first is up: 14% in 2014 versus 5% in 2013, according to a recent survey. (Source: Consumerization of IT in the Enterprise survey, 2014, 1,155 respondents) [Link TK]
Pain points
There are many different fronts to address, seemingly at once, that enabling a mobile team is very complex. It isn’t as easy as replacing a desktop with another device: almost everything will need replacement, including applications, the network infrastructure, security models and potentially Internet bandwidth may need adjustments.
Organizations that invested heavily in wired networks for many years may find that they need to rework these networks to handle wireless connections for mobile devices. And while the vast majority (76%) of firms said they are expanding their Wi-fi networks in Network World’s 2015 State of Network survey [Link TK], than means more than just deliver more ubiquitous wireless signals.
Applications built with new agile tool sets and development environments will be required, but businesses are lagging behind in this area. According to this data [Linke TK: Source: Mobility Management, IDG Enterprise/IGS, 2014], organizations do not have a set model when developing custom mobile applications: 38% said mobile apps are most commonly developed on an “as needed” basis, while 21% said they conduct internal audits of existing internal applications and then develop the most relevant mobile version.
Finally, IT departments will have to carefully understand how to secure their mobile devices and the content that resides on them.
How are companies addressing the challenges? IT leaders from four large enterprises share their mobile deployment strategies:
American Red Cross
What they did: Kept existing mainframe apps in place, built web-based front-ends to access those apps from mobile devices
Devices: Various
Traditional organizations with deep roots in a mainframe culture have an interesting journey to mobility. The American Red Cross, for example, was one of the more conservative IT shops around a few years ago. Most applications ran on its own mainframes or were installed on specially provisioned PCs that were under the thumb of the central IT organization based in Washington, D.C.
This changed when disaster response teams started to bring their personal devices to the field. The IT group attempted to standardize the devices initially, but eventually allowed employees to use their own, instead changing how applications were delivered – making them accessible from the Internet, and more browser-friendly. Translated, this means that instead of having a terminal connection to its mainframe, running an old fashioned application, they designed a new mobile app or a web interface that talks to the mainframe piece to make the experience easier. The American Red Cross still has its mainframe apps, just a different way to get to them. Throughout the process, setting user expectations was critical. “We worked with our HR department to put a few ground rules in place on using personal mobile devices, such as it is your responsibility to get good connectivity, not ours,” said John Crary, CIO for the American Red Cross. [CUT: “You have to be able to adapt to the changing mobile environment. It is moving rapidly. Businesses are going towards being more mobile-centric, and we need to be much quicker and much more adaptable.” ]
Wessex Water
What they did: Created a secure environment to access and share documents including video footage from mobile devices. The project replaced aging file transfer servers, provided tighter centralized control around who can share content and generated a full audit trail for that content.
Devices: Various
Wessex Water is a regional water and sewer utility in the UK. Its goal was to create a secure environment to access and share documents from a wide range of mobile devices including iPads, Windows tablets and smartphones. It deployed a SaaS-based secure file transfer solution, and was able to put it to multiple uses across the organization – one being to collect video footage from remote locations. Contractors hired by the utility use robotic video cameras to capture imagery inside its pipeline generating several videos each week around its water network. Prior to the SaaS solution, videos were recorded to DVDs, mailed to Wessex Water, and were manually uploaded to their servers. Now, using the vendor’s APIs, Wessex Water built automated apps that transferred these videos into its SharePoint content management system. The apps support other business workflows as well, helping the utility company “quickly meet compliance obligations while saving hundreds of work hours per week,” said John Willis, Enterprise Architect at Wessex Water.
Needham Bank
What they did: Made document workflow part of an overall mobile workspace experience; transitioned to a 100% mobile organization.
Devices: iPads and iPhones
Needham Bank, a New England financial institution, was one of the first banks to go all mobile. In 2007, they began buying iPhones. In 2010, they equipped executives with iPads when they first came on the market. “We don’t have any laptops at the bank, anyone who is out in the field has an iPad or an iPhone,” said James Gordon, the CIO at the bank. He uses a combination of apps to enable these mobile devices, including remote desktop, file transfer and mobile device management tools. “Our biggest problem is that we do more than just email on our mobile devices, and email was never designed to be a true document management tool or a file revision system. People need to have the right tools for the job, and we have built a whole suite of services both for our customers and our employees to make them more productive,” he said.
Gordon is also a big fan of reducing the number of app choices for his users and feels this is an important role for his IT department to play. You might think that a major bank would have issues with using all mobile devices, but Gordon says he did not have any push back from his auditors. Through the various security tools he uses, “we can revoke a user and they no longer have access rights. We also have extensive logs to tell who did what with which file. This can come in very handy. We had a senior executive who thought he had been hacked because one of his staffers had gotten a file. Turns out he had forgotten when he sent it. We examined our logs and found the file transfer, and pinpointed which office he was in at the time. When you can prove stuff like that, you have pretty good controls on your information, more controls than you can put on paper files that are placed in a copier.”
Organization: Revera Home Health
What they did: Used mobile devices to integrate scheduling and reporting for its field caregiver force.
Devices: BlackBerries
Mobile devices can also come into play in that time-honored tradition of automating tasks that involve massive amounts of paperwork and manual processes. This is what Halifax-based Revera Home Health faced with its field force of more than 4,000 home healthcare workers. Until a few years ago, they relied on manual methods to schedule and track which workers visited their clients’ homes and less than a tenth of them used any smartphones. “We found that a single worker calling in sick would result in more than 60 different transactions to fill that person’s shift,” said Jo-Anne Stone-Burke, a National Director at Revera Home Health.
Revera implemented a mobile-based management application based on BlackBerry smartphones that has helped improve its field communication and reporting of various home care visits. They were able to reduce missed appointments and cut down on travel time with automated GPS-based directions too. “Now we can reschedule sick calls with a touch of a button, and we have eliminated two thirds of our missed appointments, saving the company $25,000 [Canadian dollars] a month too.”
 The organization is called LaunchCode, and I have written about them here. The idea is to improve the way job candidates get screened for open positions, and to improve the supply chain of candidates, at the same time lowering the risk of a new hire for an organization.
The organization is called LaunchCode, and I have written about them here. The idea is to improve the way job candidates get screened for open positions, and to improve the supply chain of candidates, at the same time lowering the risk of a new hire for an organization.
 Chances are if you have read commentary and reviews of products and services online, you are reading lots of fakes. Various estimates put this at a third or more, either outright fakes or paid-to-post by organizations looking to game the system. In other words, buyer beware.
Chances are if you have read commentary and reviews of products and services online, you are reading lots of fakes. Various estimates put this at a third or more, either outright fakes or paid-to-post by organizations looking to game the system. In other words, buyer beware.