I hope you all had a nice break for the holidays and you are back at work refreshed and ready to go. Certainly, last year hasn’t been the best for Facebook and its disregard for its users’ privacy. But a post that I have lately seen come across my social news feed is blaming them for something that isn’t possible. In other words, it is a hoax. The message goes something like this:
Deadline tomorrow! Everything you’ve ever posted becomes public from tomorrow. Even messages that have been deleted or the photos not allowed. Channel 13 News talked about the change in Facebook’s privacy policy….
 Snopes describes this phony alert here. They say it has been going on for years. And it has gained new life, particularly as the issues surrounding Facebook privacy abuses have increased. So if you see this message from one of your Facebook friends, tell them it is a hoax and nip this in the bud now. You’re welcome.
Snopes describes this phony alert here. They say it has been going on for years. And it has gained new life, particularly as the issues surrounding Facebook privacy abuses have increased. So if you see this message from one of your Facebook friends, tell them it is a hoax and nip this in the bud now. You’re welcome.
The phony privacy message could have been motivated by the fact that many of you are contemplating leaving or at least going dark on your social media accounts. Last month saw the departure of several well known thought leaders from the social network, such as Walt Mossberg. I am sure more will follow. As I wrote about this topic last year, I suggested that at the very minimum if you are concerned about your privacy you should at least delete the Facebook Messenger app from your phone and just use the web version.
But even if you leave the premises, it may not be enough to completely cleanse yourself of anything Facebook. This is because of a new research report from Privacy International that is sadly very true. The issue has to do with third-party apps that are constructed from Facebook’s Business Tools. And right now, it seems only Android apps are at issue.
The problem has to do with the APIs that are part of these tools, and how they are used by developers. One of the interfaces specifies a unique user ID value that is assigned to a particular phone or tablet. That ID comes from Google, and is used to track what kind of ads are served up to your phone. This ID is very useful, because it means that different Android apps that are using these Facebook tools all reference the same number. What does this mean for you? Unfortunately, it isn’t good news.
The PI report looked at several different apps, including Dropbox, Shazam, TripAdvisor, Yelp and several others.
If you run multiple apps that have been developed with these Facebook tools, with the right amount of scrutiny your habits can be tracked and it is possible that you could be un-anonymized and identified by the apps you have installed on your phone. That is bad enough, but the PI researchers also found out four additional disturbing things to make matters worse:
First, the tracking ID is created whether you have a Facebook account or not. So even if you have gone full Mossberg and deleted everything, you will still be tracked by Facebook’s computers. It also is created whether your phone is logged into your Facebook account (or using other Facebook-owned products, such as What’sApp) or not.
Second, the tracking ID is created regardless of what you have specified for your privacy settings for each of the third-party apps. The researchers found that the default setting by the Facebook developers for these apps was to automatically transfer data to Facebook whenever a phone’s user opens the app. I say was because Facebook added a “delay” feature to comply with the EU’s GDPR. An app developer has to rebuild their apps with the latest version to employ this feature however. The PI researchers found 61% of the apps they tested automatically send data when they are opened.
Third, some of these third-party apps send a great deal of data to Facebook by design. For example, the Kayak flight search and pricing tool collects a great deal of information about your upcoming travels – this is because it is helping you search for the cheapest or most convenient flights. This data could be used to construct the details about your movements, should a stalker or a criminal wish to target you.
When you put together the tracking ID with some of this collected data, you can find out a lot about whom you are and what you are doing. The PI researchers, for example, found this one user who was running the following apps:
- “Qibla Connect” (a Muslim prayer app),
- “Period Tracker Clue,”
- “Indeed” (a job search app), and
- “My Talking Tom” (a children’s’ app).
This means the user could be potentially profiled as likely a Muslim mother who is looking for a new job. Thinking about this sends a chill up my spine, as it probably does with you. The PI report says, “Our findings also show how routinely and widely users’ Google ad ID is being shared with third parties like Facebook, making it a useful unique identifier that enables third parties to match and link data about an individual’s behavior.”
Finally, the researchers also found that the opt-out methods don’t do anything; the apps continue to share data with Facebook no matter what you have done in your privacy settings, or if you have explicitly sent any opt-out messages to the app’s creators.
Unfortunately, there are a lot of apps that exhibit this behavior: researchers found that Facebook apps are the second most popular tracker, after Google’s parent company Alphabet, for all free apps on the Google Play Store.
So what should you do if you own an Android device? PI has several suggestions:
First, reset your advertising ID regularly by going to Settings > Google > Ads > Reset Advertising ID. Next, go to Settings > Google > Ads > Opt out of personalized advertising to limit these types of ads that leverage your personal data. Next, make sure you update your apps to keep them current. Finally, regularly review the app permissions on your phone and make sure you haven’t granted them anything you aren’t comfortable doing.
Clearly, the real bad news about Facebook is stranger than fiction.
 The news in January about Michael Cohen’s indictments covers some interesting ground for IT managers and gives security teams something else to worry about: He allegedly paid a big data firm Redfinch Solutions to rig two online polls in then-candidate Donald Trump’s favor. To those of us who have worked with online polls and surveys, this comes as no surprise.
The news in January about Michael Cohen’s indictments covers some interesting ground for IT managers and gives security teams something else to worry about: He allegedly paid a big data firm Redfinch Solutions to rig two online polls in then-candidate Donald Trump’s favor. To those of us who have worked with online polls and surveys, this comes as no surprise. 

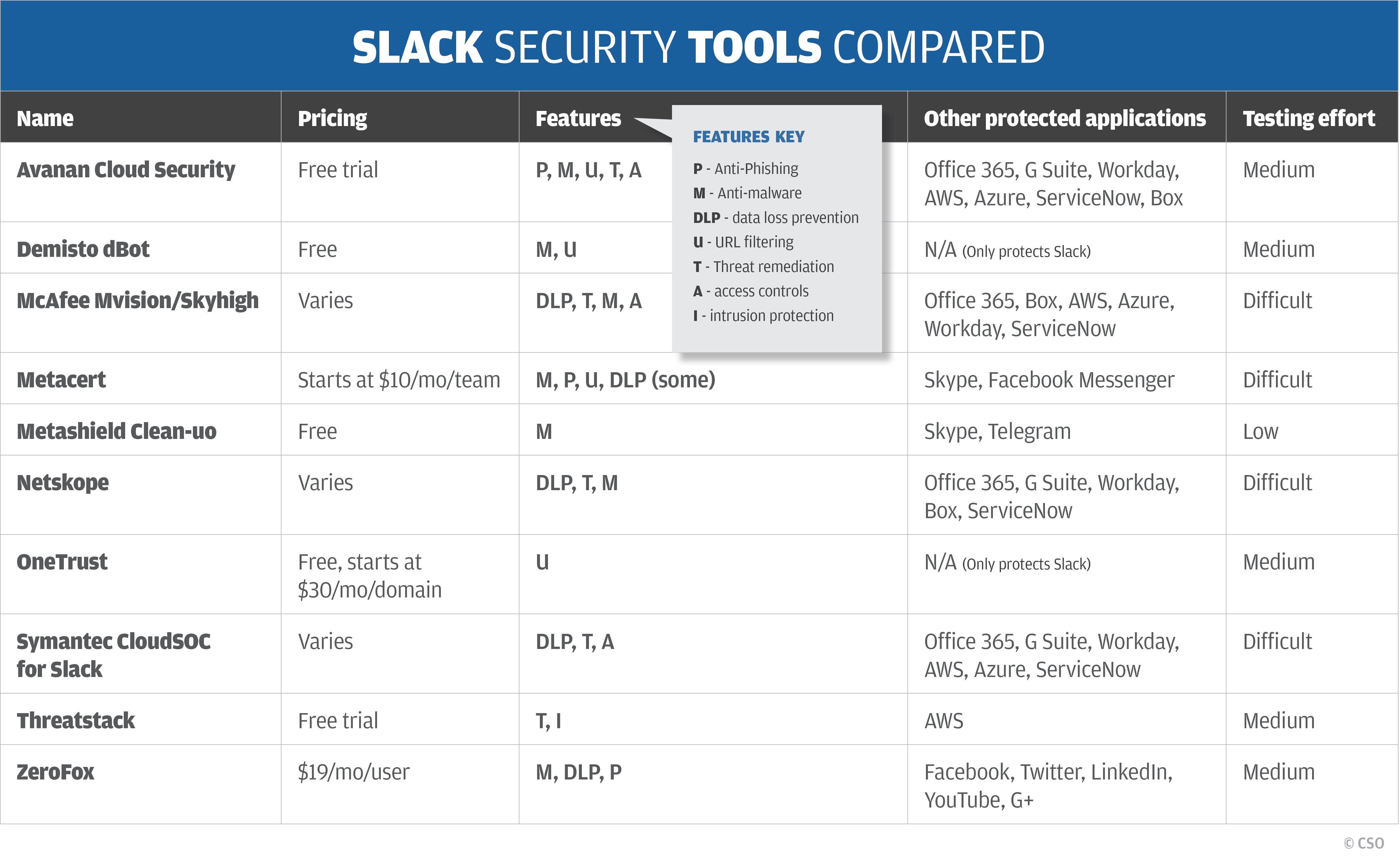
 IT and security managers have found themselves increasingly needing to better understand the world of digital forensics. This world has become more important as the probability of being breached continues to approach near-certainty, and as organizations need to better prepare themselves for legal actions and other post-breach consequences.
IT and security managers have found themselves increasingly needing to better understand the world of digital forensics. This world has become more important as the probability of being breached continues to approach near-certainty, and as organizations need to better prepare themselves for legal actions and other post-breach consequences. Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.