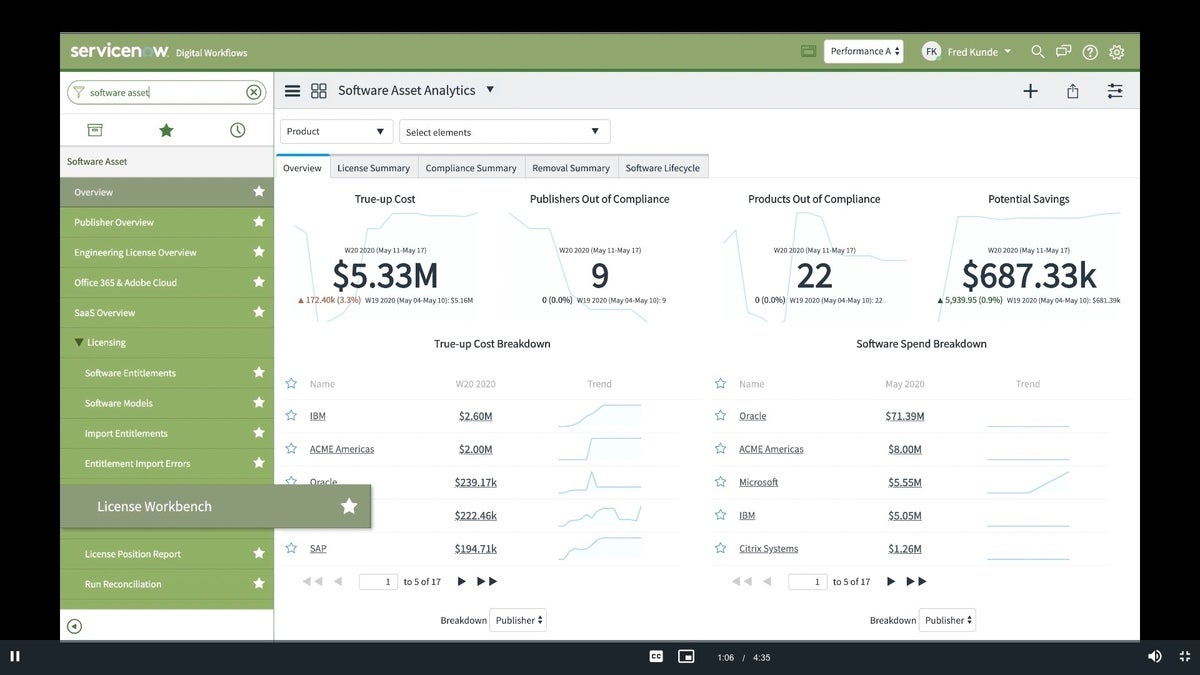
 The vulnerabilities of the Apache Log4j logging package—and the attacks they’ve drawn—have made one thing very clear: If you haven’t yet implemented a software inventory across your enterprise, now is the time to start evaluating and implementing such tools. These aren’t new — I recall testing one of the earlier products, Landesk, which is now a part of Ivanti, back in the early 1990s. In this post for Infoworld, I go into detail about how you can evaluate Ivanti and four of other leading tools from Atlassian, ServiceNow (shown above), ManageEngine and Spiceworks, why these tools are needed in modern software development organizations, how you should go about evaluating them, what their notable features are, and what these tools will cost.
The vulnerabilities of the Apache Log4j logging package—and the attacks they’ve drawn—have made one thing very clear: If you haven’t yet implemented a software inventory across your enterprise, now is the time to start evaluating and implementing such tools. These aren’t new — I recall testing one of the earlier products, Landesk, which is now a part of Ivanti, back in the early 1990s. In this post for Infoworld, I go into detail about how you can evaluate Ivanti and four of other leading tools from Atlassian, ServiceNow (shown above), ManageEngine and Spiceworks, why these tools are needed in modern software development organizations, how you should go about evaluating them, what their notable features are, and what these tools will cost.
Category Archives: Published work
Avast blog:
US President Joe Biden recently issued an executive order that will oversee various cryptocurrency efforts, including a study of whether there should be a virtual dollar-based cryptocoin, the efficacy of various future banking regulations for the Federal Reserve, and the roles for executive agencies including Treasury, Justice and Homeland Security on how to best manage crypto markets. Additionally, those of you who have already begun doing your US federal taxes might have noticed that the IRS now wants you to document your crypto holdings for the past year.
These moves show that crypto is moving quickly into the mainstream. And with mainstream acceptance also comes the criminal element. Cryptocurrency-based crime hit new levels last year, doubling the amount collected from 2020 to $14 billion. According to a new report by Chainalysis, 2021 criminal crypto transaction volumes skyrocketed by more than six times what was seen in 2020. In this post for Avast, I explore some of the other trends in crypto crime, its intersection with ransomware, and what law enforcement is doing to stop it.
FIR B2B podcast episode #153: How to Build Your “Voice Brand”

We discuss how to build a brand with the voice actors. This means deciding on what your organization “sounds like” and how you want to connect with your customers. The choice of a voice actor matters. Should you go with a commanding narrator or an approachable expert guide? “Your sonic brand is the unique soundscape that drives home the tone and personality of your brand voice,” he says. The company has created a guide to becoming a voice actor and also produces an annual “State of the Voice Over” report.
David says visual media has become crowded and notes that nearly one-third of people are primarily audio learners. “Marketers have saturated the eyes and we have to move on to the ears,” he says. “They have found that audio presents an opportunity to tell their story in a deeper, more meaningful way.”
He shares several podcast tips for B2B marketers. Commit to a small number of initial episodes or set a threshold and evaluate, but once you commit, stick with it. Decide if you want to primarily be a guest on other podcasts or host one of your own; those are very different strategies. Prepare show notes in advance, and make sure to tell a story with a beginning, middle and end. He has found that 20 minutes is the ideal podcast length as it’s the average duration of a commute, walking the dog or a daily exercise routine.
David has appeared in numerous media outlets, including Business News Network and The Globe and Mail TV, and is a frequent guest speaker at industry conferences. He is also a great resource for all things audio, such as this online recording studio and this streaming production service.
You can listen to the 24 min. podcast here.
Avast blog: Tips for securing your WordPress website
Last November, more than 1 million GoDaddy-managed WordPress customers were part of a breach that could have exposed their email addresses, private SSL keys, and admin passwords. The attacker was apparently able to operate undetected inside their networks for two whole months. This is just one data point in a long history of past exploits because WordPress has been a very rich and desirable target. There are numerous things you can do to protect your site, including using two tools that I have been using (Wordfence and MiniOrange, shown here).
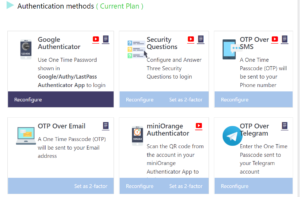 You can read more about how to secure your WordPress site on Avast’s blog. If this is a new topic for you, you shouldn’t operate WordPress without making use of these steps — even if you gradually add in individual security measures one by one.
You can read more about how to secure your WordPress site on Avast’s blog. If this is a new topic for you, you shouldn’t operate WordPress without making use of these steps — even if you gradually add in individual security measures one by one.
Avast blog: A 2022 update on data privacy legislation
Last year, Mississippi didn’t pass its privacy bill and more than a dozen states had bills that are still under consideration. Iowa, Indiana, and Oklahoma are all in the process of moving various privacy bills through their legislatures, and several other states have begun to consider new laws. Also, seven states are considering biometric information privacy legislation.
![]() The most comprehensive source remains the above annotated map from Husch Blackwell, which will link you to each state’s legislation. If you are looking for more analysis, this page from the National Conference of State Legislatures has more contextual explanations.
The most comprehensive source remains the above annotated map from Husch Blackwell, which will link you to each state’s legislation. If you are looking for more analysis, this page from the National Conference of State Legislatures has more contextual explanations.
In my latest post for Avast, I review some of the recent developments and further refinements on the three states that have enacted privacy legislation — California, Colorado and Virginia.
CSOonline: Understanding risk-based authentication
The last time I bought a suit was several years ago, in advance of my daughter’s wedding. Back in the 80s and perhaps 90s, I would wear a suit whenever I travelled or spoke at a conference. These days, not so much on either travel or suit-wearing. I actually bought two suits (whadda deal!) and I was pretty happy with the process until it came time to pay. My credit card was immediately declined. I certainly had plenty of credit limit (I think the total purchase was about $1000) but the algorithms used by my bank kicked back the transaction because it had been ages since I last bought a suit, or bought anything at a retail store for that amount of money.
This process to question my transaction is called risk-based authentication (RBA), and it has become quite common, particularly as criminals get better at compromising our accounts and as we continue to reuse our banking passwords that get phished and posted across the dark web. The banks have gotten better at investing in this tech so as not to have many false positive flags (such as my suit purchase) based on all sorts of factors. In my case, I probably still would have been challenged because I was at a location not close to my home and in a store that I hadn’t been in before. But the RBA can incorporate all sorts of other factors, such as the hardware you are using on your phone (if that is involved in the transaction), whether your typing cadence has changed (such as someone else using your computer or using a clone of your phone number), or a pattern of multiple purchases that were made earlier that day or from “impossible travel” where multiple IP addresses that are located at great distances use the same login credentials (of course, you have to be careful someone isn’t using a VPN here).
Speaking of impossible travel, back when I did travel internationally I had to remember to login to my banks and tell them where I was going. One time I forgot and my credit card dinner purchase was declined. Now most banks don’t need you to do this, thanks to better RBA.
The three credit bureaus (Experian, Equifax and Transunion) have all bought various RBA vendors over the years (41st Parameter, Kount and Iovation, respectively). Both Lexis/Nexis and Mastercard have their RBA tech too (ThreatMetrix and NuData Security). What is interesting about this group is that they handle millions of financial transactions each day, or each hour, so they can spot fraud trends more quickly. RBA has quickly grown from some wonky security tech into the more mainstream precisely for this reason.
This week I wrote a story for CSOonline where I take a closer look at 12 different RBA vendors’ offerings. I have studied these products for years, and am glad to see continued progress in their features and usability. One example is the latest offering from Ping Identity, called PingOne DaVinci. This is an identity orchestration tool that can be used to create automation routines using Visio-like flowchart diagrams. This is a big benefit, because setting up risk escalation scenarios using interlocking rule sets and policies can be difficult to debug.
Avast blog: Avoid fake Windows 11 offers with these tips
If you’ve recently received an email recommending that you upgrade to Windows 12, you probably had enough spidey-sense to delete it. You should realize this is a fake or a come-on for some piece of malware that was about to infect your computer. But what about if you got a message asking you to upgrade to Windows 11? Security researchers have tracked a malicious campaign that made use of a legitimate-sounding “windows-upgraded” domain (don’t worry, it has been neutralized since) which was used to spread RedLine Stealer malware by running a fake installer.
In my blog post for Avast, I describe the scam and ways you can check to make sure you are downloading the legit Win11 upgrade package.
Avast blog: How the IRS can do better with its digital identity program
 The US’ tax collection agency, the Internal Revenue Service (IRS), has changed course with its short-lived identity verification system that was only recently implemented. Last November, the vendor ID.me was awarded a $86 million contract to provide the exclusive authentication for all online IRS accounts. Until then, the IRS had its own account authentication service that was based on credit reporting data. The older system was to be phased out this summer.
The US’ tax collection agency, the Internal Revenue Service (IRS), has changed course with its short-lived identity verification system that was only recently implemented. Last November, the vendor ID.me was awarded a $86 million contract to provide the exclusive authentication for all online IRS accounts. Until then, the IRS had its own account authentication service that was based on credit reporting data. The older system was to be phased out this summer.
This week, things came to a head and the IRS decided to ditch their ID.me solution. I describe the chain of events, why ID.me was such a lightning rod, and what are some ways that they can gain some traction and show leadership in the decentralized identity space in my latest blog for Avast here.
Infoworld: How Roblox fixed a three-day worldwide infrastructure outage
 Last October the gaming company Roblox’s online network went down, an outage that lasted three days. The site is used by 50M gamers daily. Figuring out and fixing the root causes of this disruption would take a massive effort by engineers at both Roblox and their main tech supplier, HashiCorp. The company eventually posted an amazing analysis on a blog post at the end of January. Roblox got bitten by a strange coincidence of several events. The processes they went through to diagnose and ultimately fix things is instructive to readers that are doing similar projects, and especially if you are running any large-scale IaC installations or are a heavy user of containers and microservices across your infrastructure.
Last October the gaming company Roblox’s online network went down, an outage that lasted three days. The site is used by 50M gamers daily. Figuring out and fixing the root causes of this disruption would take a massive effort by engineers at both Roblox and their main tech supplier, HashiCorp. The company eventually posted an amazing analysis on a blog post at the end of January. Roblox got bitten by a strange coincidence of several events. The processes they went through to diagnose and ultimately fix things is instructive to readers that are doing similar projects, and especially if you are running any large-scale IaC installations or are a heavy user of containers and microservices across your infrastructure.
There are a few things to be learned from the Roblox outage that I discuss in my latest story for Infoworld.
Avast blog: How to protect your network from a future attack
A new report on how to protect your networks from attack can be a helpful document that covers a lot of different bases within the cybersecurity landscape. The report, Proactive Preparation and Hardening to Protect Against Destructive Attacks, was written by several cybersecurity analysts “based on front-line expertise with helping organizations prepare, contain, eradicate, and recover from potentially destructive threat actors and incidents,” in the words of the authors.
It contains hundreds of tips for protecting Windows deployments, including command-line strings, adjusting various group policy parameters, and other very practical tips that could indicate potential compromised systems.
I summarize a few of the more important ones in my blog post for Avast.