![]() The first thing many of us think about when it comes to the future relationship between artificial intelligence (AI) and cybersecurity is Skynet from the “Terminator” movie franchise. But I spoke with Dudu Mimram, the CTO at Telekom Innovation Laboratories when I was in Israel earlier this month, and he has a somewhat rosier view. He suggested that AI must be understood across a broader landscape, regarding how it will influence cybersecurity and how IT can use AI to plan for future security technology purchases.You can read my blog post in IBM’s Security Intelligence here.
The first thing many of us think about when it comes to the future relationship between artificial intelligence (AI) and cybersecurity is Skynet from the “Terminator” movie franchise. But I spoke with Dudu Mimram, the CTO at Telekom Innovation Laboratories when I was in Israel earlier this month, and he has a somewhat rosier view. He suggested that AI must be understood across a broader landscape, regarding how it will influence cybersecurity and how IT can use AI to plan for future security technology purchases.You can read my blog post in IBM’s Security Intelligence here.
Category Archives: security
StateTech: Best practices for single sign-on technologies for state IT departments
The days when users are required to remember numerous complex passwords may be coming to an end, as single sign-on (SSO) technologies are finally taking hold in state and local agencies. SSO tools provide a number of valuable security benefits. Among them are to better bridge the gap between cloud and on-premises servers, applications and services and they help agencies prevent the proliferation of bad passwords. You can read more details in this first piece for StateTech magazine.
Several factors have brought this about: better technology, a wider selection of identity management tools, lower-cost SSO alternatives and a heightened awareness of massive password breaches. State and local agencies should keep several important factors in mind as they consider SSO solutions, as I wrote about in a second article for StateTech magazine recently.
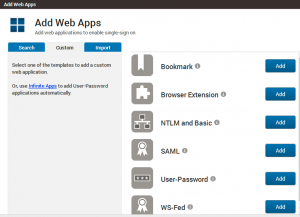 My most recent comparative review for Network World on SSO tools was done in 2015 and gave Centrify (shown here) and Okta the highest marks.
My most recent comparative review for Network World on SSO tools was done in 2015 and gave Centrify (shown here) and Okta the highest marks.
GregoryFCA blog: Stop sucking your thumb and start getting your people in the media
Ever wonder why some cyber security firms are constantly in the news? Do they offer a better solution? Know more than their competition? Do the heavy-lifting research that differentiates and substantiates their spokespeople in the minds of the media? Could be.
Or it could be that your spokespeople simply aren’t savvy enough to win media interest. In cyber security, expertise means a lot. But so does the ability to deliver powerful and memorable sound bites on breaking or trending news while empathizing with the interviewer to give the media what it wants (without a sales pitch!).
 The process begins with carefully selecting your spokesperson and then educating and grooming them to deliver a message that simultaneously entices coverage while still reflecting favorably on the reputation and expertise of your company.
The process begins with carefully selecting your spokesperson and then educating and grooming them to deliver a message that simultaneously entices coverage while still reflecting favorably on the reputation and expertise of your company.
Start with the audience. Are you shooting for general business media or the technical, vertical media? If you’re looking for coverage in the New York Times or on CNN, then you want a spokesperson who can speak at a 30,000-foot level about how an attack or topic impacts a business, family, or person.
The trades? Well, they want someone who can get into the weeds and explain the precise technical shortcomings or trap doors that a hacker or fraudster is exploiting.
Who in your organization could speak to one or both sides of the coin? Make the call and then train them to understand:
1. Media coverage is not about sales or lead gen. Rather, it’s about leveraging third-party credibility to establish thought leadership. Great spokespeople know how to quickly size up the direction of an interview and give the reporter new insights or understandings, information they can’t get elsewhere to propel their stories forward and get them filed and into print.
2. Reporters and producers want interviewees who understand the media rules of engagement. A great interview is a bit like jujitsu. A reporter comes at you from a position or angle. You need to be ready to take the barrage or use the momentum to deflect and disarm. It’s a learned skill, and one that will never be mastered without preparation and training.
3. Media interviews don’t waste time, they leverage it. Thought leaders lead by sharing and engaging with a community. There’s no more powerful way to share and engage than in leveraging the reach and credibility of the media. Building a media presence doesn’t take away from a thought leader’s job. Rather it advances it, along with the goals and objectives of their employer.
4. Charisma counts and it can be learned. Not by our spokespeople, you say? They are too nerdy, too techie. Ironically, there’s nothing wrong with getting your tech on if you’re speaking to the right audience and understand some of the rules of engagement espoused here. A 23-year old nerdy ex-hacker often conveys more authenticity than some slick, paid corporate spokesperson. The key is to harness that nerd-dom and put it work educating and engaging with the media in a real and compelling manner.
5. Sound bites matter. It’s not spin. It’s not hyperbole. The media love short, pitchy sound bites that they can use to convey meaning in a few words instead of paragraphs. “It’s ridiculous that 140 million Americans had their data stolen because a single person failed to install a patch.” You get the point. Develop those sound bites for your spokespeople before each interview and you will dramatically increase the impact of your media coverage.
Some people are naturals at speaking to the media. Most aren’t. But it is a skill your spokespeople can learn and practice before they ever talk to a reporter. The PRCoach website has a bunch of clips illustrating common interview mistakes, and has other helpful resources too. And this document lists the mistakes spokespersons make with consumer media, such as not staying on topic or losing control over the interview, or taking too long to make your point and not speaking in sound bites.
Use these five points as the backbone of their training as you shape them into go-to media sources. And maybe you can develop your own version of such security rockstars as Troy Hunt, Tavis Ormandy (who is from Google), Cris Neckar of Divergent Security and Chris Vickery that are often breaking news and being quoted by the security trade press.
Adrian Lamo, RIP
 I first met Adrian Lamo back in 2002. I was teaching a high school networking class and I thought it would be cool to have the kids experience a “real” hacker, since so many of them aspired to learn how to get into the computerized grading system that the school ran. It wasn’t a very exciting teachable moment, as I recall. But Lamo made a big impact on me, as he couch-surfed in my New York suburban apartment.
I first met Adrian Lamo back in 2002. I was teaching a high school networking class and I thought it would be cool to have the kids experience a “real” hacker, since so many of them aspired to learn how to get into the computerized grading system that the school ran. It wasn’t a very exciting teachable moment, as I recall. But Lamo made a big impact on me, as he couch-surfed in my New York suburban apartment.
Sadly, I learned that last week he died at age 37 in Wichita, KS. The cause of death hasn’t yet been determined, and he had been living in the area for the past year, according to reports. Lamo moves around alot, thanks to a rather interesting personality that could best be described as on the autism spectrum. When I met him, he had the symptoms of obsessive-compulsive disorder and was later diagnosed with Aspberger’s. One of his quirks was that it would take him a while to leave my apartment every morning: he had a sequence of steps to follow in a very specific order before he could walk out the door.
Lamo was a study in contradictions: both very bright and very socially awkward, a Sheldon Cooper before his time. He had a high sense of morality. At the time Lamo stayed with me, he had been arrested for breaking into several different computer systems, including that of the freelancer database of the New York Times. His method was to find an open Web proxy server and use that to gain entry inside a corporate network. (It is still a common entry point method, although many companies have finally figured out how to protect themselves.) He never profited financially from these attacks, instead he would often leave hints on how a company could close these proxies and improve their security. He was sentenced to house arrest for the Times attack.
At the time we met, he was called the “homeless hacker” – not because he was living on the streets, but because he was young and had no fixed address, and would go from couch to couch as the mood took him. I offered him a place to stay and a chance to get to know him better, thinking how cool could that be? Little did I know.
When I told my then-teenage daughter about his impending visit, she was rather incredulous (you have someone wanted by the police staying with us) but ultimately she was won over by his geek cred – she had a problem with her cell phone that she recalls him fixing in a matter of seconds.
Well, Lamo went on get a degree in journalism, ironically enough. He was very connected to the tech trade press, and Brian Krebs recalls his various interactions with him in this post.
Lamo is remembered in various tributes in the past few days with his role in the Wikileaks/Cablegate case of 2010, when he divulged the name of Private Manning to the feds as the leaker. Both then and now, his decision was vilified in the hacking community, with numerous online threats.
I had a chance to speak to Lamo back in 2011 and recorded the interview for ReadWrite, where I was working at the time. It covers a lot of ground:
He has some very wise comments about the importance of government secrecy, and the freedoms that it enables for us all. Lamo saw the Manning case from the other side, as a case that would be eventually remembered supporting our freedoms. It was a real issue for him, because as a hacker he could certainly understand what Manning was trying to do, but as someone who also understood the role of our military he couldn’t in good conscience allow her to leak all that data. When Manning contacted Lamo he had a crisis of conscience and made his decision. He struggled over harming Manning, whom he considered a friend, or harming countless others who would be placed at risk because of Manning’s leaks. He wishes Manning had come to him before making the documents public.
This is certainly an interesting position for a hacker to take, to be sure. He was vilified in the hacker community because of it, but I think he made the right decision. “Who would have thought that when we first met ten years ago that I would have been involved in the single biggest intelligence leak in history,” he told me. How true.
He continued to work as a security consultant, helping corporations understand better security practices as well as going out on the speaking circuit. Ironically, his preferred method of communications more recently was FedEx! “I’m a little bit of a Luddite these days,” he said.
Lamo left this planet far too soon. He was a very smart guy and had a very solid moral compass, and those two traits guided his actions all his short life. I am sad that he is no longer with us, and hope that his life can be noted and celebrated for his accomplishments, verve and significance.
iBoss blog: The Network Printer Threat is Still a Thing, Sadly
I have written about the dangers of network printers for many years, and show how these seemingly innocent devices can be exploited. Lately there have been additional vulnerabilities and new attempts to use printers as a source of network attacks, so it is time to return to this topic with additional warnings.
Perhaps the biggest recent exploit is one that can be found in Lexmark models. Security researchers in December 2017 were able to enumerate more than a thousand different printers online that had no passwords whatsoever used to secure them. The attack is dirt simple: once you find the printer’s IP address, you connect to its webserver and within a few seconds can choose your own password. Once that is done, you can install your own exploit software and wreak all sorts of havoc. Lexmark, when contacted by reporters, claimed this was a feature and not a bug, as it gave its customers flexibility in setting up their printers. I think otherwise, and suggest you fix this post-haste.
Unfortunately, Lexmark is by no means alone in this department. Other security researchers in Germany have discovered all sorts of vulnerabilities in many different vendors’ printers, including HP, Lexmark, Dell, Brother, Konica and Samsung. A total of more than 60,000 individual devices may be at risk to a variety of issues, including password tampering, buffer overflows, and remote code execution. To help understand the depth of their analysis, they created a set of tools called the Printer Exploitation Toolkit which can be used to launch the attacks against these vulnerabilities, so you can assess your own portfolio of printers.
You might complain that developing such a tool can only make printers more of a potential threat if the tool is used by evildoers. Perhaps, but let’s hope its creation can help remove the vulnerable printers from the exploit column.
Why are network printers still an issue? One reason has to do with how printers are purchased by many businesses. “Ownership is [a] factor,” says Ed Wingate, vice president and general manager of JetAdvantage Solutions at HP and quoted in this article about the situation. “Printers are shared devices, and it’s often unclear whether they belong to IT, facilities, or the team responsible for purchasing them. This leads to ambiguity over who should control the security of each device,” he says. Maybe so, but it is ultimately IT’s responsibility, no matter who brings them in the door.
Another reason has to do not with the printer itself but vulnerabilities in how Windows looks for printers across the network. It has to do with how printer drivers are installed on Windows computers, and how attackers can abuse the privileges connected to these drivers. Back in 2016, researchers found a watering-hole attack that was eventually patched. The researchers wrote in this blog post, “These devices can be hard to patch, hard to monitor and can quickly become a persistent blind-spot for security operations. This is a good reason to monitor all of your internal traffic regardless of the device type.”
 Some printer vendors are taking security more seriously, and certainly HP has tried to get their own printers under control in the past several years. You should download their white paper which describes numerous vulnerabilities and how to protect your printers. The paper also has a handy guide to which of their printer models support which of the security features mentioned. Other vendors should follow their lead and produce similar documents.
Some printer vendors are taking security more seriously, and certainly HP has tried to get their own printers under control in the past several years. You should download their white paper which describes numerous vulnerabilities and how to protect your printers. The paper also has a handy guide to which of their printer models support which of the security features mentioned. Other vendors should follow their lead and produce similar documents.
Clearly, we still have a long way to go before we can assume that all of our network printers are free of abuse from hackers. But as the paperless office is never going to happen, we will always have need for printers, and that means we have to spend some effort in securing them better.
CSO Online: Inside RSA’s state-of-the-art fraud intelligence command center
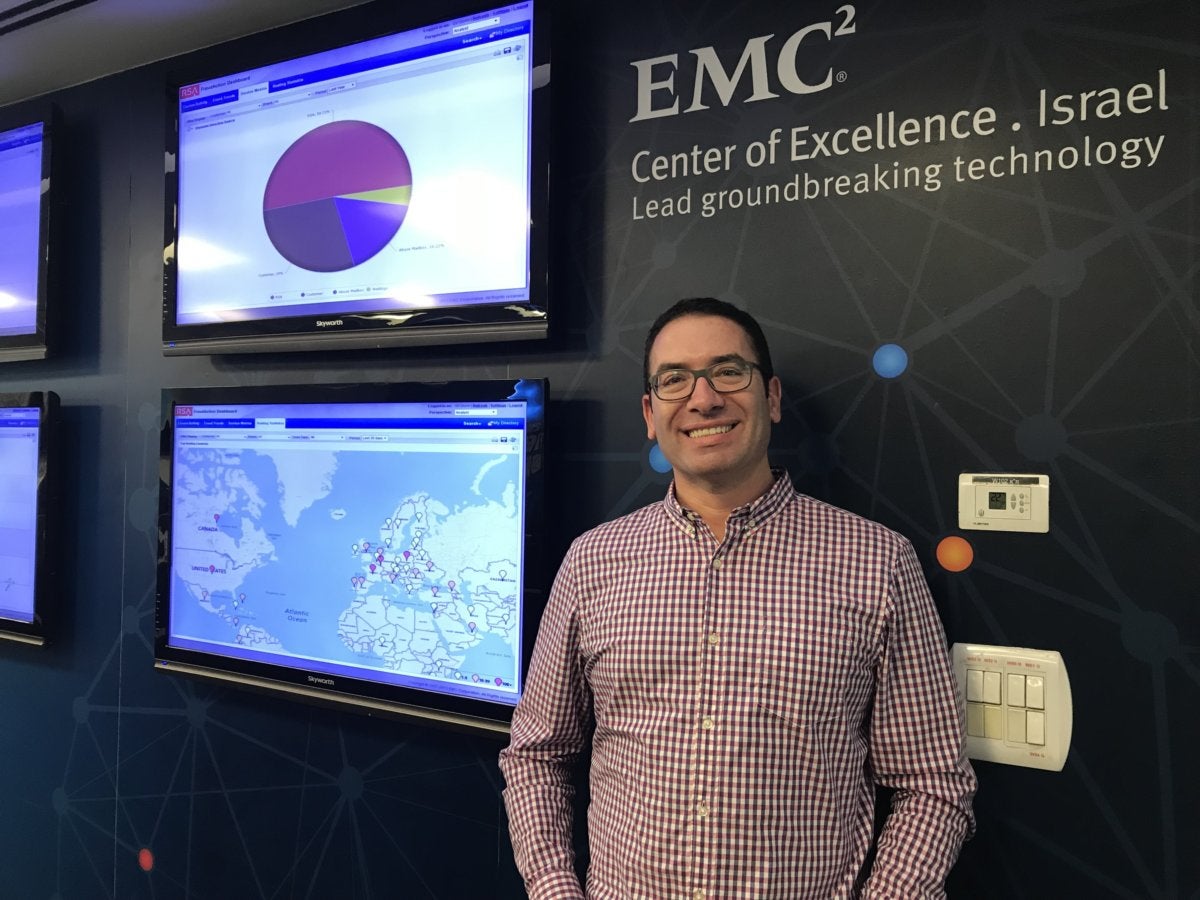 As cybercriminals get better at compromising financial accounts and stealing funds, vendors are beefing up their defensive tools to prevent fraud and abuse. I had an opportunity while I was in Israel to visit Daniel Cohen (shown here) of RSA’s Anti-Fraud Command Center (AFCC), the nerve center of a division that is devoted to protecting consumers’ financial records and funds. The AFCC is an example of what a state-of-the-art web threat and fraud intelligence operation looks like. Here is my report for CSO Online.
As cybercriminals get better at compromising financial accounts and stealing funds, vendors are beefing up their defensive tools to prevent fraud and abuse. I had an opportunity while I was in Israel to visit Daniel Cohen (shown here) of RSA’s Anti-Fraud Command Center (AFCC), the nerve center of a division that is devoted to protecting consumers’ financial records and funds. The AFCC is an example of what a state-of-the-art web threat and fraud intelligence operation looks like. Here is my report for CSO Online.
CSO Online: 10 questions to answer before running a capture the flag (CTF) contest
 Capture-the-flag (CTF) contests have been around for decades. One of the longest-running and more popular series began at the Vegas DEFCON show in 1996 and attracts thousands of participants. Running your own CTF contest can build security skills and help identify new internal and external talent. In this article for CSO Online, I compare CTFs with cyber ranges such as CyberGym (shown here) so you can learn what types of challenges you need to include for your own contest, how to make the contest run smoothly, and other logistics to consider.
Capture-the-flag (CTF) contests have been around for decades. One of the longest-running and more popular series began at the Vegas DEFCON show in 1996 and attracts thousands of participants. Running your own CTF contest can build security skills and help identify new internal and external talent. In this article for CSO Online, I compare CTFs with cyber ranges such as CyberGym (shown here) so you can learn what types of challenges you need to include for your own contest, how to make the contest run smoothly, and other logistics to consider.
BrianMadden.com: An introduction to FIDO
 Many years ago, the idea of making a more universal multi-factor authentication (MFA) token seemed like a good idea. Back then, hardware tokens were proliferating, and so were the number of logins for different web-based services. Out of that era, the Fast Identity Online (FIDO) Alliance was created in July 2012 and publicly announced in February 2013 to try to bring some standards to this arena. Since then, the FIDO standards have gone through several revisions and extensions, and more than 100 vendors have joined the non-profit association, including some of the largest names in the identity and authentication business.
Many years ago, the idea of making a more universal multi-factor authentication (MFA) token seemed like a good idea. Back then, hardware tokens were proliferating, and so were the number of logins for different web-based services. Out of that era, the Fast Identity Online (FIDO) Alliance was created in July 2012 and publicly announced in February 2013 to try to bring some standards to this arena. Since then, the FIDO standards have gone through several revisions and extensions, and more than 100 vendors have joined the non-profit association, including some of the largest names in the identity and authentication business.
While it has taken a while to gain traction, FIDO is now at an inflection point and has reached sufficient maturity that deploying it isn’t a matter of if, but when for most enterprises.
Finding (cyber) false flags
I am a big reader of spy novels and my latest fascination is the Red Sparrow trilogy, of which the first book has been made into an upcoming movie. In one of the novels the spies attempt to penetrate an Iranian nuclear project, with one of the characters, an American CIA operative, posing as a Russian nuclear engineer. This situation is called a false flag.
The idea behind a false flag is when a spy (or group of them) represent themselves as from some other country to confuse the enemy. Back in the days of naval warfare, ships changed their flag they were flying deliberately to sneak into an enemy’s midst. Hence the name.
 While spy novels love to talk about false flags, they do have some basis in reality, at least some situations. One is the Lavon affair which refers to a failed Israeli covert operation that was conducted in Egypt in the summer of 1954 and run by Pinhas Lavon, shown here. There are numerous other ops that are on other lists that show the depths that intelligence agencies will go through to misrepresent themselves.
While spy novels love to talk about false flags, they do have some basis in reality, at least some situations. One is the Lavon affair which refers to a failed Israeli covert operation that was conducted in Egypt in the summer of 1954 and run by Pinhas Lavon, shown here. There are numerous other ops that are on other lists that show the depths that intelligence agencies will go through to misrepresent themselves.
The same is true in the modern cybersecurity era. We have false flags all the time when malware attacks a target and mislead its origins. Then researchers try to pick it apart and figure out its attribution. Does the code resemble something they have already seen? Are the names of the variables or documentation written in a particular (non-coding) language, or using cultural or other references? Are there targets of a particular political or national significance? These and other factors make malware attribution more art than science.
I was reminded of this when I read this piece from the Talos blog about trying to figure out who was behind the Olympic Destroyer malware that we saw last month. Several security bloggers have come out with Russian attribution, but the Talos team says, not so fast. Yes, there are similarities to Russia state-sponsored sources, but it isn’t a slam dunk and there are also other suspects that could be the source of this malware.
Sadly, for cybersecurity it isn’t as easy as switching a flag to figure these things out. And reports about malware’s source need to be careful to ensure that we have the right attribution, otherwise we might be retaliating against the wrong people.
Security Intelligence blog: An Interview With IBM Master Inventor James Kozloski on His New Security Patent: The Cognitive Honeypot
 What does a master IBM inventor who typically models brain activity have to do with enterprise security? If you ask James Kozloski, you won’t get a quick answer, but it will definitely be an interesting one.
What does a master IBM inventor who typically models brain activity have to do with enterprise security? If you ask James Kozloski, you won’t get a quick answer, but it will definitely be an interesting one.
Kozloski, who is a manager of computational neuroscience and multiscale brain modeling for IBM Research, is always coming up with new ideas. He was recently part of a team of IBMers that received a security patent for a cognitive honeypot. If you don’t know what that is, check out my story on IBM’s SecurityIntelligence blog for details with this very interesting inventor.