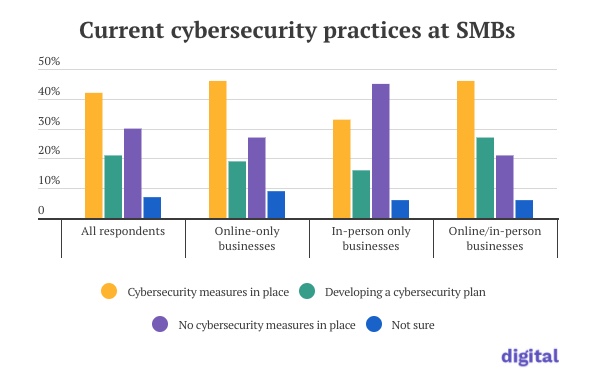
CNN had me review a bunch of VPN services for their Underscored site. I looked at 11 different products. I don’t have to tell you why you should use a VPN. But no product can 100% handle the trade-off among three parameters: anonymity, or the ability to move online without anyone knowing who you are; privacy, or the ability to keep your own data to yourself; and security, or to prevent your computers and phones and other gear from being compromised by a criminal. You can’t do all three completely well unless you go back to pen and paper and the Pony Express. Using a VPN will help with all three aspects, and some are better than others at balancing all three.
My two favorites were Mullvad.net and IVPN.net. Both use a novel idea to ensure that they don’t know anything about you — when you download their software, you are assigned a random string of characters that you use to identify yourself. No email necessary. If you don’t want to use your credit card, you can pay via alt-coins too. Consider this a “single-factor” authentication. That means no password is required once you have entered your code, it is unlikely that anyone can guess this code or find it on the dark web (unless you reuse it, which you shouldn’t), and there is little chance anyone could connect it back to you even if they did manage to get a hold of the code in a breach.
Both vendors don’t have the largest server networks (that title is shared by Hotspot Shield, Private Internet Access, ExpressVPN and CyberGhost). But each of these are owned by corporate entities that play fast and loose with your private data (Aura and Kape Technologies). If you want to spend more time understanding the privacy issues, check out Yael Grauer’s excellent analysis for Consumer Reports Digital Lab here.
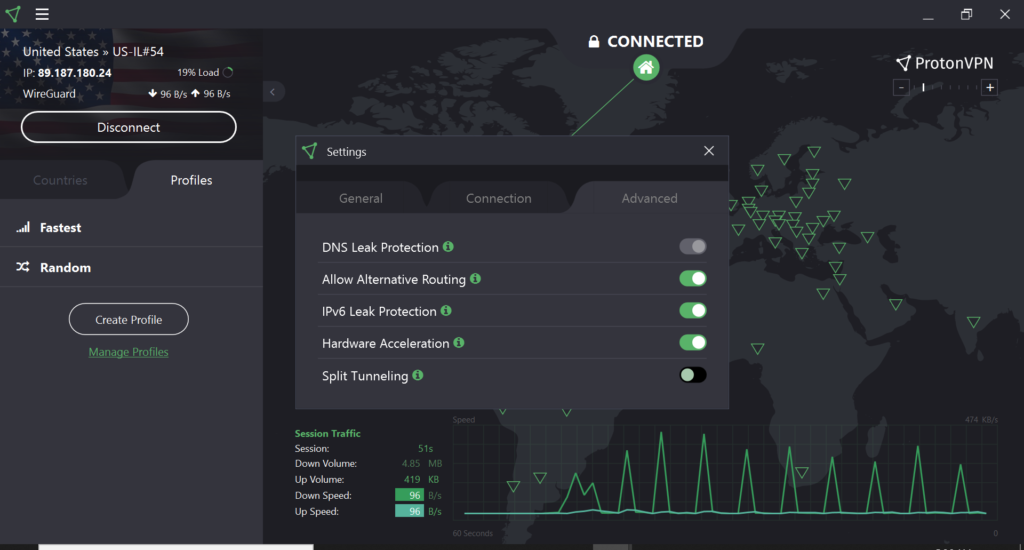 Not on my recommended list is the VPN that I have been using for the past several years — ProtonVPN (shown above). I am of two minds here. On the plus side, I have a fond spot in my nerd heart for Proton, the Swiss company that was an early proponent of encrypted email. But the VPN product is slower, more expensive, harder to use and more of an “OG” VPN that requires emails and credit cards to subscribe. Yael’s report also mentions some privacy difficulties with the service, as well as those well-advertised services mentioned above that have leaked data or aren’t as transparent as they claim to be.
Not on my recommended list is the VPN that I have been using for the past several years — ProtonVPN (shown above). I am of two minds here. On the plus side, I have a fond spot in my nerd heart for Proton, the Swiss company that was an early proponent of encrypted email. But the VPN product is slower, more expensive, harder to use and more of an “OG” VPN that requires emails and credit cards to subscribe. Yael’s report also mentions some privacy difficulties with the service, as well as those well-advertised services mentioned above that have leaked data or aren’t as transparent as they claim to be.
If you leave home, you need to run some kind of VPN. Period.
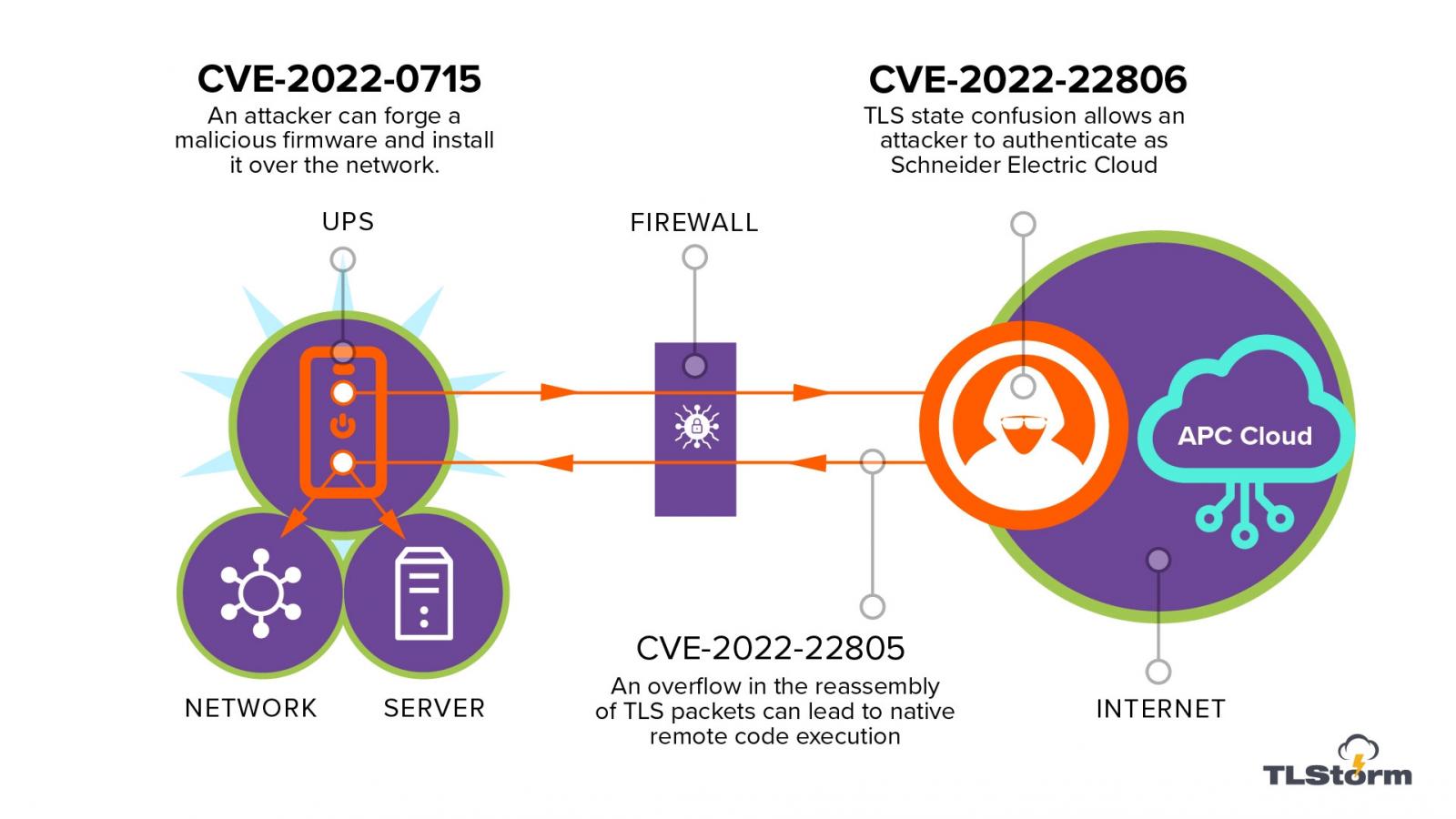 Security researchers have uncovered a new series of threats that are targeting uninterrupted power supply (UPS) units. These threats can result in malware attacking the computers connected to the same networks through a variety of clever mechanisms.
Security researchers have uncovered a new series of threats that are targeting uninterrupted power supply (UPS) units. These threats can result in malware attacking the computers connected to the same networks through a variety of clever mechanisms.