Magecart, the notorious credit card stealing cybercrime syndicate, is once again in the news. It is the gift that keeps on giving – it has recently taken root in three different online restaurant ordering websites: MenuDrive, Harbortouch, and InTouchPOS. The malware was found in more than 300 restaurants that used them and exposed more than 50,000 paid orders. The malware was present in some of these systems for many months before they were discovered. Indeed, some attacks began last November and are still active.
Category Archives: Published work
How Fortnite spurred innovations in architectural technology
For someone who has been deeply steeped in technology for most of my career, I am woefully ignorant about computer games. I have written about this aspect of my life before, but today’s topic is how one game studio has had a breakout success in developing some very serious non-gaming business applications.
 The company is Epic Games, most notably known for its Fortnite brand. Perhaps you have played it, or your kids have played it. Fortnite is built using the Unreal Engine, which has been around for decades and is now on its fifth version. Epic was smart with UE in getting it established as the premier 3D visualization tool, and it is used in all sorts of business applications. One of them caught my interest, when I watched this video from one of my favorite You Tube creators about the building of the Xi’an soccer stadium. The architects of the stadium used UE to pre-visualize how the seating sight lines would work, how the roof would be constructed, and other design aspects of the stadium. It is still under construction. We are building a more modest soccer stadium here in St. Louis, so I have a bit of stadium envy here.
The company is Epic Games, most notably known for its Fortnite brand. Perhaps you have played it, or your kids have played it. Fortnite is built using the Unreal Engine, which has been around for decades and is now on its fifth version. Epic was smart with UE in getting it established as the premier 3D visualization tool, and it is used in all sorts of business applications. One of them caught my interest, when I watched this video from one of my favorite You Tube creators about the building of the Xi’an soccer stadium. The architects of the stadium used UE to pre-visualize how the seating sight lines would work, how the roof would be constructed, and other design aspects of the stadium. It is still under construction. We are building a more modest soccer stadium here in St. Louis, so I have a bit of stadium envy here.
Anyway, Epic was smart with spinning out UE from Fortnite. First, it is free to download and get started. Yes, there are license fees if you want to do more with it, but you can figure it out and use most of its features without spending any money. Second, there is a huge dev community to support your efforts: discussion forums, loads of documentation, and professional education options too. UE is being taught in numerous colleges across the world. For example, there is this entire online curriculum. These efforts have paid off, and now there are numerous games that independent developers have built in UE.
Before I get to that, here is a short diversion into the world of film pre-viz. When I was living in LA back in the early aughts, I got to meet Dan Gregoire of Halon Entertainment. Halon is one of the pre-eminent pre-viz shops in the entertainment space, and has worked on numerous blockbuster movies. The concept is similar to what the architects are doing: if you can represent what will be shown on screen digitally, you can help a director figure out what camera and lighting and actors are going to be filmed and save a lot of time and money. I asked Dan about UE and turns out he has been using this tool for more than five years, first adopting it for his work for War for the Planet of the Apes. “It is the core foundation of our pre-viz pipeline,” he told me. “We use it for all sorts of things, including as a virtual art department, LED stage content and final pixel game cinematics.” Coincidentally, today they are part of a conference being held in Burbank featuring experts from Nvidia, UE and Microsoft.
But let’s turn back to this field of architectural technology. As architects have gotten comfortable with digital tools, things like doing pre-viz for the Xi’an stadium make a lot of sense. If you can create a digital copy of your building and experiment with various changes before you pour the first foundation footing, you can save a lot of money and build a better building too.
”In the past, architects had to put huge financial resources aside to hire experts who specialize in using visualization tools,” writes this one blog. “The Unreal Engine removes all this from the equation. It is an easy-to-use tool with medium hardware requirements and supports real-time rendering and experimental visualization.” In effect, UE has made rendering more of a commodity to designers and made pre-viz more approachable even for smaller design studios. Epic has this website that will provide all sorts of case studies and links to resources. There is the Atlantic Technological University in Dublin, which actually offers a three-year BS degree in this area. That is impressive.
It is ironic in a way. Just as our construction industry supply chains are getting choked, digital technology can help cut down on mistakes and help build better buildings. “Real-time technology is the future,” says Dan. “All it took was for the technology to be accessible from a business model perspective, and having Epic license it for free for non-game content was a big step.”
Avast blog: The importance of patching
I’ve often made recommendations about patching your systems. Patching is a simple concept to explain: Keeping all your various digital components (hardware, software, and networking infrastructure) up to date with the most recent versions. However, it can be easier said than done – this is due to the fact that our day-to-day operations have become complex systems that interconnect and intersect in ways that are hard to predict. In this blog post for Avast, I review some of the benefits of timely patching, how to get a patching program established and operational, and some notable failures about patching over the years.
SC Magazine: The coming passkey revolution
 The war on passwords has entered a new and more hopeful era: their final battle for existence. The challenger is the passkey. Let’s talk about why this is happening now, what exactly the passkey is, and how the victory might just finally be in sight. The goal is a worthy one — according to Verizon DBIR 2022 report, 80% of data breaches still begin with a phishing or Man-in-the-Middle attack, using hijacked account credentials to take over an account. Spoiler alert: passkeys can help big-time in this fight.
The war on passwords has entered a new and more hopeful era: their final battle for existence. The challenger is the passkey. Let’s talk about why this is happening now, what exactly the passkey is, and how the victory might just finally be in sight. The goal is a worthy one — according to Verizon DBIR 2022 report, 80% of data breaches still begin with a phishing or Man-in-the-Middle attack, using hijacked account credentials to take over an account. Spoiler alert: passkeys can help big-time in this fight.
Passkeys use a set of cryptographic keys – meaning a long string of digits – in a way that you, the user, doesn’t have to remember or type anything additional. They have been adopted by the major endpoint vendors (Google, Apple and Microsoft), and in my post for SC Magazine I describe how they work.
Avast blog: Explaining malicious PDF attachments
The next time someone sends you an email with a PDF attachment, take a moment before clicking to open it. While most PDF files are benign, hackers have recently been using PDFs in new and very lethal ways. Malicious PDFs are nothing new. In my post for Avast’s blog here, I explain their history and how two news items have shown that they are still an active threat vector and being exploited in new and interesting ways, such as this invoice which has different amount due items depending on the particular reader used to view the file.
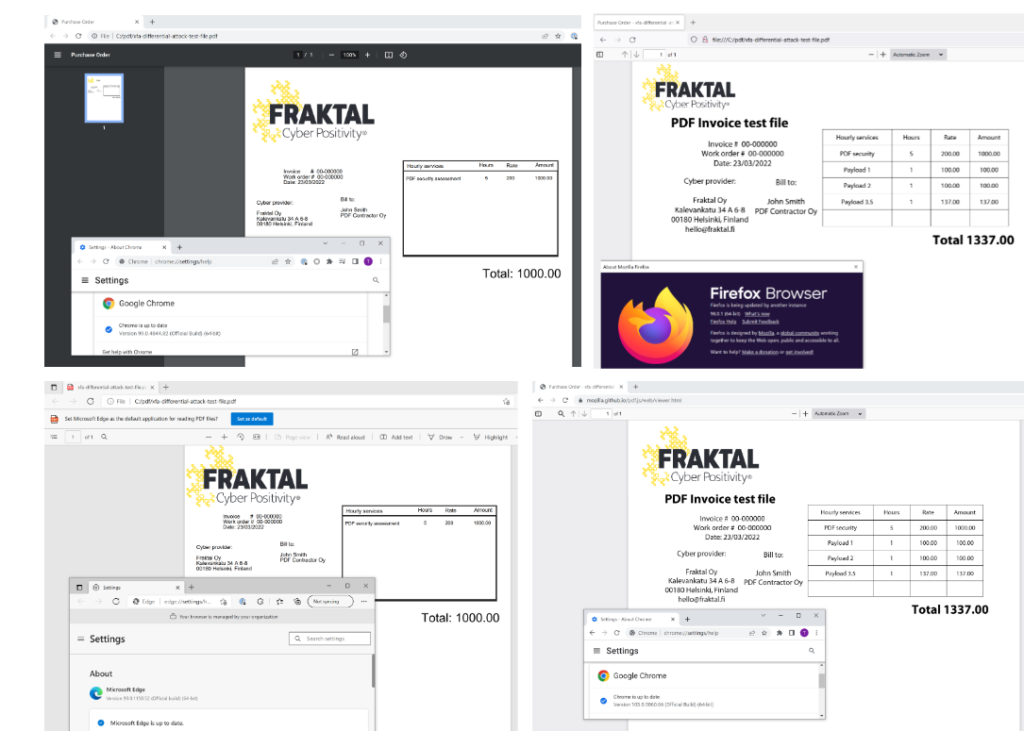
Avast blog: A new way to fight Office macro-based malware
Microsoft has made it a bit harder for macro viruses to proliferate with a recent change to its default macro security policies. Malware-infected Microsoft Office macros have been around for close to three decades. These exploits involve inserting code into a seemingly innocuous Word or Excel macro, which is then downloaded by an unsuspecting user by clicking on a phishing lure or just a simple misdirected email attachment. Recently, Microsoft changed the default settings, making it harder both for this type of malware to spread and also harder for IT managers who have to figure out how to manage their legitimate macro users. And then, they rolled back these changes, based on user complaints. I explain the details in this post for Avast’s blog.
A better treatment, with lots of specifics on Office group policy settings, can be found in Susan Bradley’s CSO piece here.
GoodAccess VPN review: A new twist on an old security tool designed for the smaller business
 There are lots of reasons to use a VPN for business: to improve your access speeds, to avoid state-sponsored blocks or tracking of your browsing movements, and to segregate your business traffic when working remotely or home from prying eyes, And while there are numerous VPNs that focus on larger enterprises or for individual consumers, the middle ground is poorly served. This is the target segment that GoodAccess, a Czech-based company, is after. They sponsored a review of their product, and I think they deliver in terms of preserving anonymity, privacy, and security and have superior product features that make it particularly attractive for smaller businesses, such as its main dashboard shown here.
There are lots of reasons to use a VPN for business: to improve your access speeds, to avoid state-sponsored blocks or tracking of your browsing movements, and to segregate your business traffic when working remotely or home from prying eyes, And while there are numerous VPNs that focus on larger enterprises or for individual consumers, the middle ground is poorly served. This is the target segment that GoodAccess, a Czech-based company, is after. They sponsored a review of their product, and I think they deliver in terms of preserving anonymity, privacy, and security and have superior product features that make it particularly attractive for smaller businesses, such as its main dashboard shown here.
Avast blog: New deepfake video effort discovered
 Since I wrote about the creation and weaponization of deepfake videos back in October 2020, the situation has worsened. Earlier this month, several European mayors received video calls from Vitali Klitschko, the mayor of Kyiv. These calls turned out to be impersonations (can you tell which image above is real and which isn’t?), generated by tricksters. The mayor of Berlin, Franziska Giffey, was one such recipient and told reporters that the person on these calls looked and sounded like Klitschko, but he wasn’t an actual participant. When Berlin authorities checked with their ambassador, they were told Klitschko wasn’t calling her. Fake calls to other mayors around Europe have since been found by reporters.
Since I wrote about the creation and weaponization of deepfake videos back in October 2020, the situation has worsened. Earlier this month, several European mayors received video calls from Vitali Klitschko, the mayor of Kyiv. These calls turned out to be impersonations (can you tell which image above is real and which isn’t?), generated by tricksters. The mayor of Berlin, Franziska Giffey, was one such recipient and told reporters that the person on these calls looked and sounded like Klitschko, but he wasn’t an actual participant. When Berlin authorities checked with their ambassador, they were told Klitschko wasn’t calling her. Fake calls to other mayors around Europe have since been found by reporters.
Were these calls deepfakes? Hard to say for sure. I cover the issues and update you on the advances, if you can call them that, about deepfake tech for my Avast blog today.
Avast blog: RSocks criminal botnet taken down
Last week, the US Department of Justice announced the takedown of Russian IoT botnet and proxy service for hire RSocks. Working with various European law enforcement agencies, the FBI used undercover purchases of the site’s services to map out its infrastructure and operations. RSocks compromised its victims by brute forcing attacks on various IoT devices as well as smartphones and computers.
Network World: How to reduce cloud costs
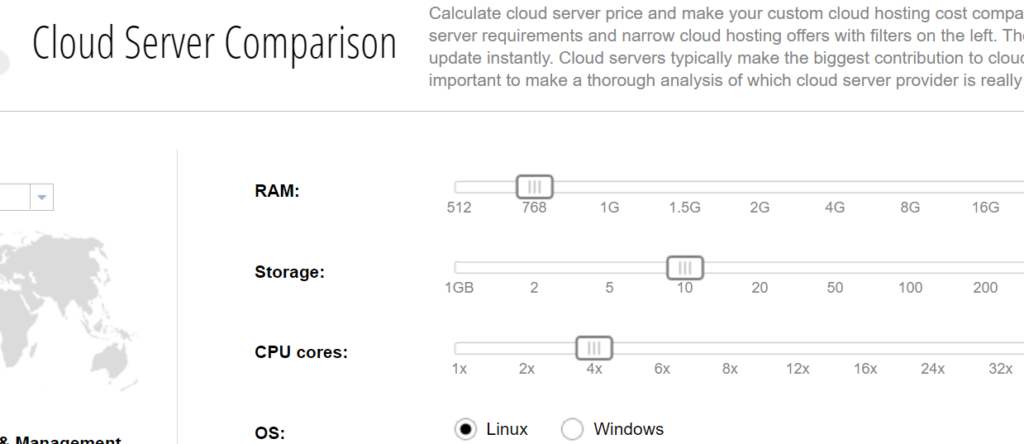 The more workloads that you migrate to the cloud, the more difficult it becomes to predict monthly cloud costs. While it is great that you’re only paying for the services you need, trying to parse your monthly bill requires the skills of a CPA, a software engineer, a commodities trader and a sharp eye for the details. There are numerous helpful tools and services to help, and also several reasons to consider using them. You might be in the market to switch to a new provider in order to add features or because you aren’t happy with your provider’s downtime or level of customer support.
The more workloads that you migrate to the cloud, the more difficult it becomes to predict monthly cloud costs. While it is great that you’re only paying for the services you need, trying to parse your monthly bill requires the skills of a CPA, a software engineer, a commodities trader and a sharp eye for the details. There are numerous helpful tools and services to help, and also several reasons to consider using them. You might be in the market to switch to a new provider in order to add features or because you aren’t happy with your provider’s downtime or level of customer support.
You can read my post for Network World here, where I provide details on more than a dozen different offerings. (Cloudorado is shown above.)