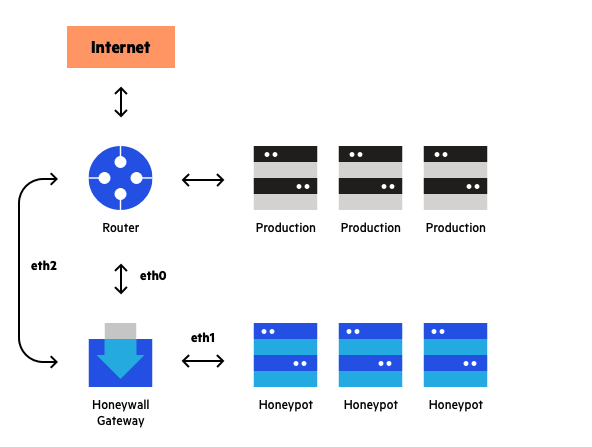
 The original idea behind honeypot security was to place a server on some random Internet link and sit back and wait until some hacker happened by. The server’s sole purpose would be to record the break-in attempt — it would not be part of a normal applications infrastructure. Then a researcher would observe what happened to the server and what exploit was being used. A honeypot is essentially bait (passwords, vulnerabilities, fake sensitive data) that’s intentionally made very tempting and accessible. The goal is to deceive and attract a hacker who attempts to gain unauthorized access to your network.
The original idea behind honeypot security was to place a server on some random Internet link and sit back and wait until some hacker happened by. The server’s sole purpose would be to record the break-in attempt — it would not be part of a normal applications infrastructure. Then a researcher would observe what happened to the server and what exploit was being used. A honeypot is essentially bait (passwords, vulnerabilities, fake sensitive data) that’s intentionally made very tempting and accessible. The goal is to deceive and attract a hacker who attempts to gain unauthorized access to your network.
In this blog for Network Solutions, I describe their role in modern network security, compare the features of various commercial and open source products, and provide a series of tips on how to pick the right kind of deception product to fit your business’ needs.