If you run the IT security for your organization, you probably are feeling two things these days. First, you might be familiar with the term “box fatigue,” meaning that you have become tired of purchasing separate products for detecting intrusions, running firewalls, and screening endpoints for malware infections. Secondly, you are probably more paranoid too, as the number of data breaches continues unabated, despite all these disparate tools to try to keep attackers at bay.
I spent some time last month with the folks behind the Tachyon endpoint management product. The vendor is 1E, which isn’t a name that you often see in the press. They are based in London with a NYC office, and have several large American corporations as customers. While they paid me to consult with them, I came away from my contact with their product genuinely impressed with their approach, which I will try to describe here.
A lot of infosec products try to push the metaphor of searching for a needle (such as malware) in a haystack (your network). That notion is somewhat outdated, especially as malware authors are getting better at hiding their infections in plain sight, reusing common code that is part of the Windows OS or chaining together what seems like innocuous routines into a very destructive package. These blended threats, as they are known, are very hard to detect, and often live inside your network for days or even months, eluding most security scanners. This is one of the reasons why the number of breaches continues to make news.
What Tachyon does isn’t trying to find that needle, but instead figures out that first you need to look for something that doesn’t appear to be a piece of hay. That is an important distinction. In the memorable words of Donald Rumsfeld, there are unknown unknowns that you can’t necessary anticipate. He was talking about the fog of war, which is a good analogy to tracking down malware.
 The idea behind Tachyon is to help you discover all sorts of ad hoc and serendipitous things out of your collection of computers and networks that you may not even have known required fixing. Often, issues that start out with some security problem end up becoming general IT operations related when they need to be fixed. Tachyon can help bridge that gap.
The idea behind Tachyon is to help you discover all sorts of ad hoc and serendipitous things out of your collection of computers and networks that you may not even have known required fixing. Often, issues that start out with some security problem end up becoming general IT operations related when they need to be fixed. Tachyon can help bridge that gap.
Today’s enterprise has an increasingly more complex infrastructure. As companies move to more virtual and cloud-based servers and more agile development, there are more moving parts that can be very brittle. Some cloud-based businesses have hundreds of thousands of servers running: if just a small fraction of a percent of that gear has a bug, it becomes almost impossible to ferret out and fix. This post on LinkedIn’s engineering blog is a good case in point. “Any service that is live 24/7 is in a state of change 24/7, and with change comes failures, escalations, and maybe even sleepless nights spent firefighting.” And that is just dealing with production systems, rather than any deliberate infections.
Unlike more narrowly-focused endpoint security products, Tachyon operates in a wider arena that responds to a lot of different events that deal with the entire spectrum of IT operations– not just related to your security posture. Does it matter if you have been infected with malware or have a problem because of an honest mistake by someone with setting up their machine? Not really: your environment isn’t up to par in either situation.
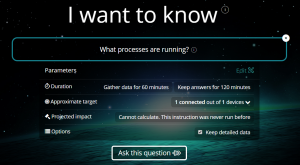
So how does Tachyon do this? It is actually quite simple to explain, and let me show you their home screen:
Does that query box at the top remind you of something? Think about Tachyon as what Google was trying to do back in the late 1990s. Back then, no one knew about search engines. But we quickly figured out that its simple query interface was more than an affectation when we got some real utility out of those queries. That is where we are today with Tachyon: think of it as the search tool for finding out the health of your network. You can ask it a question, and it will tell you what is happening.
Many security products require specialized operators that need training to navigate their numerous menus and interpret their results. What Tachyon is trying to do is to use this question-and-answer rubric that can be used by almost anyone, even a line manager, to figure out what is ailing your network.
But having a plain Jane home page is just one element of the product. The second important difference with Tachyon is how it automates finding and updating that peculiar piece of hay in the stack. I won’t get into the details here, but Tachyon isn’t the only tool in the box that has automation. While there are many products that claim to be able to automate routine IT functions, they still require a lot of manual intervention. Tachyon takes its automation seriously, and puts in place the appropriate infrastructure so it can automate the non-routine as well, to make it easier for IT staffs to do more with fewer resources. Given the reduced headcounts in IT, this couldn’t come at a better time.
If you would like to learn more about Tachyon and read the full review that I wrote about the product, download the PDF here and you’ll see why I think highly of it. And here is a short video about my thoughts on the product.
Now I realize that having 1E as a client could bias my thinking. But I think they are on to something worthwhile here. if you are looking for way to respond and resolve network and endpoint problems at scale, they deserve a closer look.
Another point of view, doing more extensive testing than I did but coming to similar conclusions:
http://penconsultants.com/blog/tachyon-a-security-pros-paradise/