When I was at the Citrix Synergy show in Orlando last week, I was interested in tracking down their announcement about their securing web browsing product. I have been interested in secure browsing technology for several years now, mainly because the web browser has been a major infection vector and allows malware to be transported to millions of computers through phishing, man-in-the-middle, SQL injection and countless other attacks. Securing the browsing channel could be a way to stop this madness.
A few years ago, I did a review of several products for Network World, looking at Authentic8 Silo, Spoon’s BrowerStudio, Invincea’s FreeSpace and Spikes AirGap. While the review is outdated, the process that I went through to try to test these products made me realize that securing everyone’s web browsers is a lot harder problem that it first appears.
Typically, these products offer one of two approaches: One way is they sandbox, virtualize or otherwise contain the browsing session via several different methods so that any Web pages or online content can’t reach the actual desktop that is being used to surf the Web. A second approach is to replace the usual Internet Explorer, Firefox or Chrome browser software with a specialized browser that is locked down and has limited functionality.
The secure browser might give up surfing speed or not view a more complex website properly. And you still have someone’s regular browser sitting on their PC that could cause trouble. Not to mention that some of these early products did a lousy job at protection.
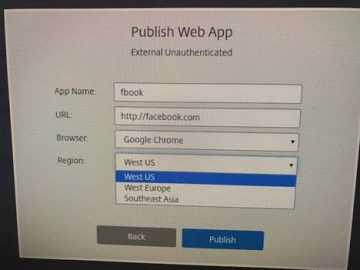 Citrix has had a secure browser service as part of its Cloud offerings for about a year now. It uses a combination of sandboxing and locking down the browser environment in an interesting way.
Citrix has had a secure browser service as part of its Cloud offerings for about a year now. It uses a combination of sandboxing and locking down the browser environment in an interesting way.
While the motivation behind its old and new products is similar, the execution is different, as Brett Waldman in their product marketing department explained to me at the show. The older secure browser (shown here) allows you to secure a specific web app. You set up an instance that ties a specific browser version (such as Chrome or Edge) to a specific app (such as Facebook), and you can add a data center that the browser request will originate from. Once this is done, every time you launch that instance, you will bring up an HTML v5 copy of a browser and taken to Facebook’s website under just those circumstances. The actual browsing is happening inside Citrix Cloud, not on your local PC. It is a way to lock things down with a specific app. You can think of it as running a stripped-down version of Receiver just for this one app.
But that isn’t good enough and doesn’t handle a lot of situations. What happens if you want more control over your browsing experience that goes beyond specifying a browser type and originating location? Or if you want to run a machine that isolates the browser from the rest of the applications? Or just want to try out a secure browser without loading a lot of Citrix infrastructure? That is where the app layering technology that Unidesk provides comes in handy, and that was what announced this week with Secure Browsing Essentials which will be available on the Azure Marketplace. By having layers, you can select exactly which bits and pieces of the browser you want to enable, so if you don’t want Flash or want to block pop-ups or downloads of executable files, you don’t assemble those pieces of code.
Citrix has other “Essentials” products on the Azure Marketplace, which makes it easy for anyone to get started with this technology. PJ Hough, Citrix SVP of Product, said the new Citrix Secure Browser Essentials will be available before the end of the year, with pricing starting at $180 per year (with a three-year subscription for a minimum of 50 subscribed users). Waldman said that this product “gives us a different route to market and to be able to satisfy these other use cases. Because it is on the Marketplace, it can also be more self-service and reach a different kind buyer, even within an existing Citrix customer.”