 I have been using various forms of WordPress as my main blogging and website platform for several years now and am generally quite fond of it. It has taken me a while to feel comfortable with tweaking it, mainly because the defaults just do so much of the job that I don’t really need to be a WP expert.
I have been using various forms of WordPress as my main blogging and website platform for several years now and am generally quite fond of it. It has taken me a while to feel comfortable with tweaking it, mainly because the defaults just do so much of the job that I don’t really need to be a WP expert.
Earlier this month I moved my main strominator.com blog from being hosted on WordPress.com to my own domain. It went surprisingly well, with just a few hiccups: my database file was nearing the limit of 8 MB which meant I had to split it up to get the entries imported. And it took about a day to reconstruct my full database of categories and labels.
Why bother moving it over? There are several alternatives to the free hosting on WP.com. GoDaddy offers WP hosting packages where they will even automatically update the WP software for you at the same price that they host a minimal server. I don’t recommend this option: WP updates happen frequently and many plug-ins stop working with the newer versions.
Another reason not to use GoDaddy hosting: its uptime isn’t what it could be. I use the service from Anturis to keep track of downtime, and it is quick and free to set this up
Speaking of plug-ins, that is the main reason for moving your blog to your own domain. You have full control over what you can install and how to fine-tune the site’s features. And while it is great to be able to add plug-ins, you need to realize that this also increases your attack surface area pretty substantially. The WP plug-in directory site currently lists 29,000 different ones. Some of them have been downloaded by millions of users and are quite useful, such as Akismet for blocking spam or Jetpack, which adds a number of features.
So like many other things in tech, freedom comes at a price of being more proactive about securing your servers. So before you consider a move to your own domain and be more motivated about securing your WP site, read this article by David Brumbaugh about WP as a secure apps platform over on Dice.
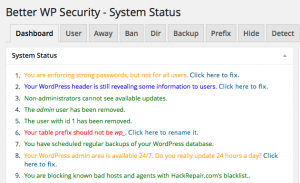
He suggests a number of things to do, including using the “Better WP Security” plug-in to get started. I downloaded this plug-in and found it amazingly comprehensive, and interesting in how many places that I had to tweak and adjust to make sure that my directories weren’t browsable, my defaults weren’t obvious, and other nips and tucks here and there. The screen shot above shows just the main dashboard display of “to-do” items to fix.