You have heard the arguments for using IPv6 for decades, but here is a novel reason: it is all about getting better network performance. A recent study from Cloudflare’s network operations shows that an IPv6 network can operate 25ms to 300ms faster than over an IPv4 network. That isn’t theory: that is what they actually observed. These numbers are corroborated with studies from LinkedIn and Facebook, although Sucuri did a test last year that shows about the same in terms of web surfing.
Part of the debate here has to do with what constitutes performance. As Geoff Huston at the Australian RIPE network coordination center writes, you have to look carefully at what is actually being tested. He mentions two factors: overall network reliability (meaning connection attempts, dropped packets and so forth) and round-trip time over the resulting network paths of the two protocols. Just because you use the same network endpoints for your tests doesn’t mean that your IPv4 packets will travel over the same path as your IPv6 ones.
Huston shows that IPv6 reliability rates have been steadily increasing, especially as native IPv6 implementations have grown, replacing tunneling and other compromises that have had higher failure rates in the past. And round-trip times have been improving, with IPv6 being faster than IPv4 about half of the time.
Cloudflare also observed that some smartphones can save on IPv4/v6 translation times if they can connect over IPv6 directly. Such phones are becoming the norm on T-Mobile and Orange mobile networks, for example. This agrees with Huston’s research: the more native IPv6 implementations on your endpoints and routers you can use, the better your overall performance.
But there is a second reason why you should consider IPv6, and that has to do with security. After all, this is a security-related blog so we talk about this for a moment. In the past, there have been articles such as this one in Security Intelligence that warn, ”The thing is, despite IPv6 having been around for almost 20 years now, few security professionals truly understand it.” Other bloggers point out that enabling native IPv6 will make your network less secure, because more embedded devices (like webcams and industrial controls) can become compromised (think Murai and WannaCry). That post suggests that most network administrators should turn off native IPv6, to reduce the potential attack surface.
I disagree. This is because IPv6 has several key technological innovations over older IPv4: it avoids NAT, has stateless or serverless address autoconfiguration, has a better protocol header to minimize processing time, uses simpler administration of IPSec conversations, is more efficient with QoS implementations, has a better multicast and anycast support and uses other more modern technologies. Taken together, the good news is that you could also get some big security improvements, if you deploy IPv6 properly across your enterprise.
Supporting IPv6 isn’t a simple matter of turning on the protocol across your network: you have to migrate segments, servers, routers and endpoints carefully and understand how you can establish a full end-to-end native implementation of the protocol. But if you do it correctly, you could have a better performing and more secure network as a result.
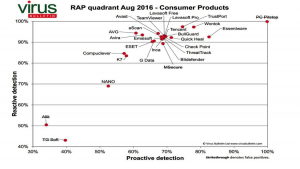
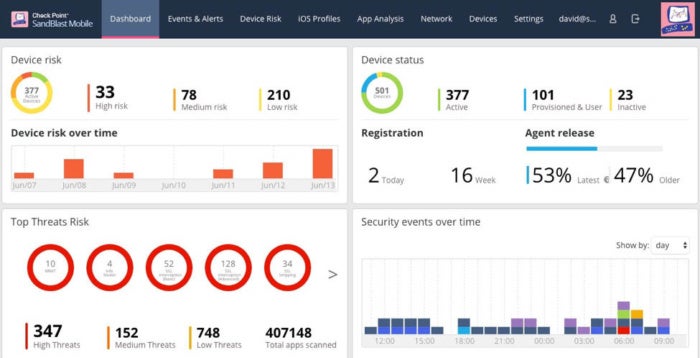
 Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.
Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.
 In the old days — perhaps one or two years ago — security professionals were fond of saying that you need multiple authentication factors (MFAs) to properly secure login identities. But that advice has to be tempered with the series of man-in-the-middle and other malware exploits on MFAs that nullify the supposed protection of those additional factors. Times are changing for MFA, to be sure.
In the old days — perhaps one or two years ago — security professionals were fond of saying that you need multiple authentication factors (MFAs) to properly secure login identities. But that advice has to be tempered with the series of man-in-the-middle and other malware exploits on MFAs that nullify the supposed protection of those additional factors. Times are changing for MFA, to be sure.
