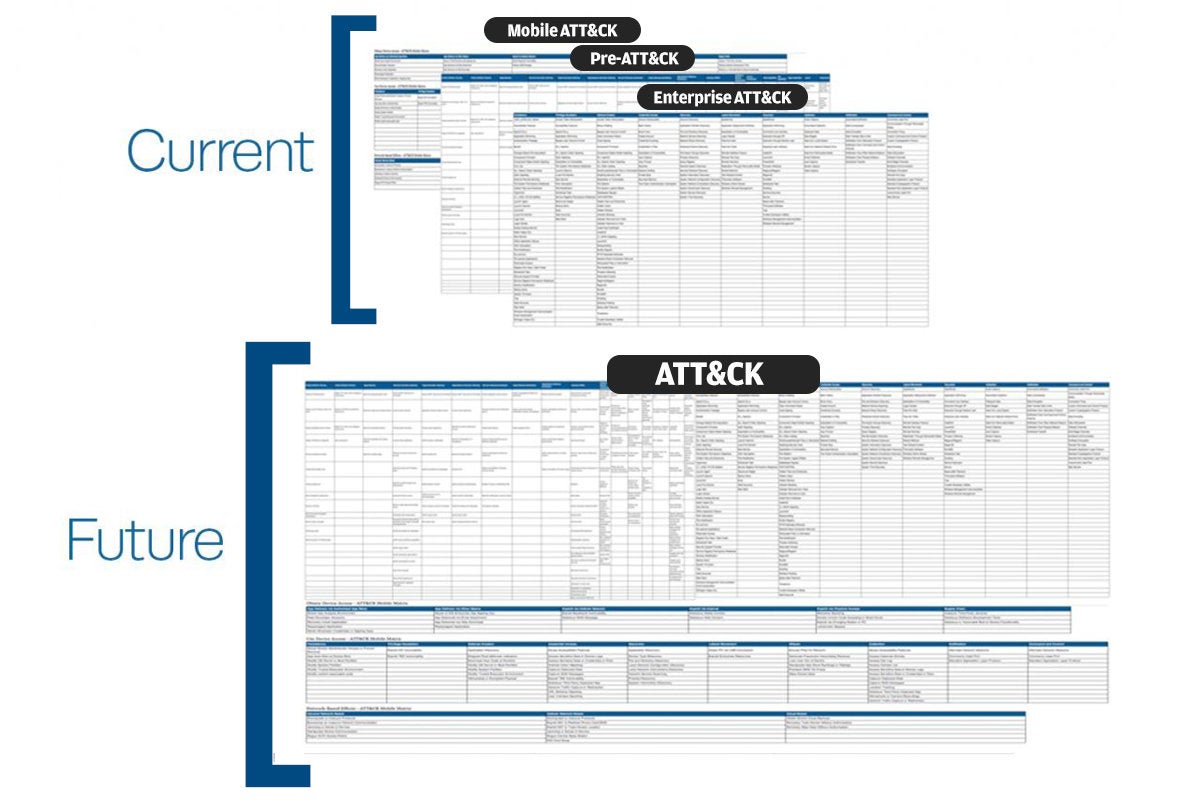
 The ATT&CK framework, developed by Mitre Corp., has been around for five years and is a living, growing document of threat tactics and techniques that have been observed from millions of attacks on enterprise networks. The funky acronym stands for Adversarial Tactics, Techniques, and Common Knowledge. It began as an internal project and morphed into this behemoth of a public knowledge base. In this post for CSOonline, I discuss what ATT&CK is, how it can be used, and how some of the numerous security vendors and consultants have picked up on using it.
The ATT&CK framework, developed by Mitre Corp., has been around for five years and is a living, growing document of threat tactics and techniques that have been observed from millions of attacks on enterprise networks. The funky acronym stands for Adversarial Tactics, Techniques, and Common Knowledge. It began as an internal project and morphed into this behemoth of a public knowledge base. In this post for CSOonline, I discuss what ATT&CK is, how it can be used, and how some of the numerous security vendors and consultants have picked up on using it.
Category Archives: Published work
Security Intelligence blog: Understanding the Relationship Between AI and Cybersecurity
![]() The first thing many of us think about when it comes to the future relationship between artificial intelligence (AI) and cybersecurity is Skynet from the “Terminator” movie franchise. But I spoke with Dudu Mimram, the CTO at Telekom Innovation Laboratories when I was in Israel earlier this month, and he has a somewhat rosier view. He suggested that AI must be understood across a broader landscape, regarding how it will influence cybersecurity and how IT can use AI to plan for future security technology purchases.You can read my blog post in IBM’s Security Intelligence here.
The first thing many of us think about when it comes to the future relationship between artificial intelligence (AI) and cybersecurity is Skynet from the “Terminator” movie franchise. But I spoke with Dudu Mimram, the CTO at Telekom Innovation Laboratories when I was in Israel earlier this month, and he has a somewhat rosier view. He suggested that AI must be understood across a broader landscape, regarding how it will influence cybersecurity and how IT can use AI to plan for future security technology purchases.You can read my blog post in IBM’s Security Intelligence here.
StateTech: Best practices for single sign-on technologies for state IT departments
The days when users are required to remember numerous complex passwords may be coming to an end, as single sign-on (SSO) technologies are finally taking hold in state and local agencies. SSO tools provide a number of valuable security benefits. Among them are to better bridge the gap between cloud and on-premises servers, applications and services and they help agencies prevent the proliferation of bad passwords. You can read more details in this first piece for StateTech magazine.
Several factors have brought this about: better technology, a wider selection of identity management tools, lower-cost SSO alternatives and a heightened awareness of massive password breaches. State and local agencies should keep several important factors in mind as they consider SSO solutions, as I wrote about in a second article for StateTech magazine recently.
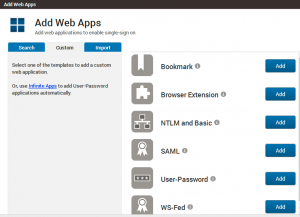 My most recent comparative review for Network World on SSO tools was done in 2015 and gave Centrify (shown here) and Okta the highest marks.
My most recent comparative review for Network World on SSO tools was done in 2015 and gave Centrify (shown here) and Okta the highest marks.
iBoss blog: The Network Printer Threat is Still a Thing, Sadly
I have written about the dangers of network printers for many years, and show how these seemingly innocent devices can be exploited. Lately there have been additional vulnerabilities and new attempts to use printers as a source of network attacks, so it is time to return to this topic with additional warnings.
Perhaps the biggest recent exploit is one that can be found in Lexmark models. Security researchers in December 2017 were able to enumerate more than a thousand different printers online that had no passwords whatsoever used to secure them. The attack is dirt simple: once you find the printer’s IP address, you connect to its webserver and within a few seconds can choose your own password. Once that is done, you can install your own exploit software and wreak all sorts of havoc. Lexmark, when contacted by reporters, claimed this was a feature and not a bug, as it gave its customers flexibility in setting up their printers. I think otherwise, and suggest you fix this post-haste.
Unfortunately, Lexmark is by no means alone in this department. Other security researchers in Germany have discovered all sorts of vulnerabilities in many different vendors’ printers, including HP, Lexmark, Dell, Brother, Konica and Samsung. A total of more than 60,000 individual devices may be at risk to a variety of issues, including password tampering, buffer overflows, and remote code execution. To help understand the depth of their analysis, they created a set of tools called the Printer Exploitation Toolkit which can be used to launch the attacks against these vulnerabilities, so you can assess your own portfolio of printers.
You might complain that developing such a tool can only make printers more of a potential threat if the tool is used by evildoers. Perhaps, but let’s hope its creation can help remove the vulnerable printers from the exploit column.
Why are network printers still an issue? One reason has to do with how printers are purchased by many businesses. “Ownership is [a] factor,” says Ed Wingate, vice president and general manager of JetAdvantage Solutions at HP and quoted in this article about the situation. “Printers are shared devices, and it’s often unclear whether they belong to IT, facilities, or the team responsible for purchasing them. This leads to ambiguity over who should control the security of each device,” he says. Maybe so, but it is ultimately IT’s responsibility, no matter who brings them in the door.
Another reason has to do not with the printer itself but vulnerabilities in how Windows looks for printers across the network. It has to do with how printer drivers are installed on Windows computers, and how attackers can abuse the privileges connected to these drivers. Back in 2016, researchers found a watering-hole attack that was eventually patched. The researchers wrote in this blog post, “These devices can be hard to patch, hard to monitor and can quickly become a persistent blind-spot for security operations. This is a good reason to monitor all of your internal traffic regardless of the device type.”
 Some printer vendors are taking security more seriously, and certainly HP has tried to get their own printers under control in the past several years. You should download their white paper which describes numerous vulnerabilities and how to protect your printers. The paper also has a handy guide to which of their printer models support which of the security features mentioned. Other vendors should follow their lead and produce similar documents.
Some printer vendors are taking security more seriously, and certainly HP has tried to get their own printers under control in the past several years. You should download their white paper which describes numerous vulnerabilities and how to protect your printers. The paper also has a handy guide to which of their printer models support which of the security features mentioned. Other vendors should follow their lead and produce similar documents.
Clearly, we still have a long way to go before we can assume that all of our network printers are free of abuse from hackers. But as the paperless office is never going to happen, we will always have need for printers, and that means we have to spend some effort in securing them better.
CSO Online: Inside RSA’s state-of-the-art fraud intelligence command center
 As cybercriminals get better at compromising financial accounts and stealing funds, vendors are beefing up their defensive tools to prevent fraud and abuse. I had an opportunity while I was in Israel to visit Daniel Cohen (shown here) of RSA’s Anti-Fraud Command Center (AFCC), the nerve center of a division that is devoted to protecting consumers’ financial records and funds. The AFCC is an example of what a state-of-the-art web threat and fraud intelligence operation looks like. Here is my report for CSO Online.
As cybercriminals get better at compromising financial accounts and stealing funds, vendors are beefing up their defensive tools to prevent fraud and abuse. I had an opportunity while I was in Israel to visit Daniel Cohen (shown here) of RSA’s Anti-Fraud Command Center (AFCC), the nerve center of a division that is devoted to protecting consumers’ financial records and funds. The AFCC is an example of what a state-of-the-art web threat and fraud intelligence operation looks like. Here is my report for CSO Online.
CSO Online: 10 questions to answer before running a capture the flag (CTF) contest
 Capture-the-flag (CTF) contests have been around for decades. One of the longest-running and more popular series began at the Vegas DEFCON show in 1996 and attracts thousands of participants. Running your own CTF contest can build security skills and help identify new internal and external talent. In this article for CSO Online, I compare CTFs with cyber ranges such as CyberGym (shown here) so you can learn what types of challenges you need to include for your own contest, how to make the contest run smoothly, and other logistics to consider.
Capture-the-flag (CTF) contests have been around for decades. One of the longest-running and more popular series began at the Vegas DEFCON show in 1996 and attracts thousands of participants. Running your own CTF contest can build security skills and help identify new internal and external talent. In this article for CSO Online, I compare CTFs with cyber ranges such as CyberGym (shown here) so you can learn what types of challenges you need to include for your own contest, how to make the contest run smoothly, and other logistics to consider.
BrianMadden.com: An introduction to FIDO
 Many years ago, the idea of making a more universal multi-factor authentication (MFA) token seemed like a good idea. Back then, hardware tokens were proliferating, and so were the number of logins for different web-based services. Out of that era, the Fast Identity Online (FIDO) Alliance was created in July 2012 and publicly announced in February 2013 to try to bring some standards to this arena. Since then, the FIDO standards have gone through several revisions and extensions, and more than 100 vendors have joined the non-profit association, including some of the largest names in the identity and authentication business.
Many years ago, the idea of making a more universal multi-factor authentication (MFA) token seemed like a good idea. Back then, hardware tokens were proliferating, and so were the number of logins for different web-based services. Out of that era, the Fast Identity Online (FIDO) Alliance was created in July 2012 and publicly announced in February 2013 to try to bring some standards to this arena. Since then, the FIDO standards have gone through several revisions and extensions, and more than 100 vendors have joined the non-profit association, including some of the largest names in the identity and authentication business.
While it has taken a while to gain traction, FIDO is now at an inflection point and has reached sufficient maturity that deploying it isn’t a matter of if, but when for most enterprises.
CSO Online: How to protect your network from PowerShell exploits
 Hikers living off the land make use of existing nutrients and water sources to survive in the wilderness. In hacker parlance, the term “survive in the wilderness” means they cover their tracks and make use of tools and code that already exist on targeted endpoints. This hides their exploits by making them look like common administrative tasks so that detection tools can’t easily find them. Welcome to the world of PowerShell-based attacks.
Hikers living off the land make use of existing nutrients and water sources to survive in the wilderness. In hacker parlance, the term “survive in the wilderness” means they cover their tracks and make use of tools and code that already exist on targeted endpoints. This hides their exploits by making them look like common administrative tasks so that detection tools can’t easily find them. Welcome to the world of PowerShell-based attacks.
PowerShell has become increasingly sophisticated and in an article I wrote for CSO Online, I show you how attackers can leverage this language for their own evil purposes.
iBoss blog: The Many Forms of Cryptocurrency Exploits
 While the prices on cryptocurrencies have been all over the place in recent months, it is certainly attracting a different kind of attention from the criminal world that views them as malware opportunities. These attacks take numerous forms, including stealing funds from digital wallets, attacking currency exchanges, deploying hidden mining and initial coin offering (ICO) exploits.
While the prices on cryptocurrencies have been all over the place in recent months, it is certainly attracting a different kind of attention from the criminal world that views them as malware opportunities. These attacks take numerous forms, including stealing funds from digital wallets, attacking currency exchanges, deploying hidden mining and initial coin offering (ICO) exploits.
The first major exploit was seen by the DAO joint Ethereum investment fund back in 2016, which suffered a DDoS attack and eventually had to shut down. While that grabbed major headlines, there have been other, less-publicized attacks on exchanges. I look at some of the more recent examples in my post for iBoss’ blog here.
iBoss blog: Ten ways to harden your WordPress servers
 One of the weak points in your enterprise may be something that you haven’t paid much attention to, your WordPress servers. When you think more critically about the issue, there are a lot of exposed attack surfaces: a Web server running PHP scripts and accessing a SQL database. Sadly, criminals have long recognized this target and have begun to focus more of their efforts on exploiting WordPress servers. Indeed, this story from last summer’s DefCon conference demonstrated how hackers were able to locate a fresh new WP site within 30 minutes of going online. In my latest post for the iBoss blog, I talk about ways to make them more secure, such as adding the WordFence plug-in shown here.
One of the weak points in your enterprise may be something that you haven’t paid much attention to, your WordPress servers. When you think more critically about the issue, there are a lot of exposed attack surfaces: a Web server running PHP scripts and accessing a SQL database. Sadly, criminals have long recognized this target and have begun to focus more of their efforts on exploiting WordPress servers. Indeed, this story from last summer’s DefCon conference demonstrated how hackers were able to locate a fresh new WP site within 30 minutes of going online. In my latest post for the iBoss blog, I talk about ways to make them more secure, such as adding the WordFence plug-in shown here.