A new browser privacy study by Professor Doug Leith, the Computer Science department chair at Trinity College is worth reading carefully. Leith instruments the Mac versions of six popular browsers (Chrome, Firefox, Safari, Edge, Yandex and Brave) to see what happens when they “phone home.” All six make non-obvious connections to various backend servers, with Brave connecting the least and Edge and Yandex (a Russian language browser) the most. How they connect and what information they transmit is worth understanding, particularly if you are paranoid about your privacy and want to know the details.
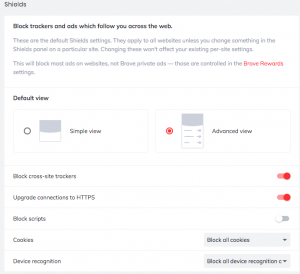 If you aren’t familiar with Brave, it is built on the same Chromium engine that Google uses for its browser, but it does have a more logical grouping of privacy settings that can be found under a “Shields” tab as you can see in this screenshot. It also comes with several extensions for an Ethereum wallet and support for Chromecast and Tor. This is why Brave is marketed as a privacy-enhanced browser.
If you aren’t familiar with Brave, it is built on the same Chromium engine that Google uses for its browser, but it does have a more logical grouping of privacy settings that can be found under a “Shields” tab as you can see in this screenshot. It also comes with several extensions for an Ethereum wallet and support for Chromecast and Tor. This is why Brave is marketed as a privacy-enhanced browser.
Brave scored the best in Leith’s tests. It didn’t track originating IP addresses and didn’t share any details of its browsing history. The others tagged data with identifiers that could be linked to an enduser’s computer along with sharing browsing history with backend servers. Edge and Yandex also saved data that persisted across a fresh browser installation on the same computer. That isn’t nice, because this correlated data could be used to link different apps running on that computer to build an overall user profile.
One problem is the search bar autocomplete function. This is a big time saver for users, but it also a big privacy invasion depending on what data is transmitted back to the vendor’s own servers. Safari generated 32 requests to search servers and these requests persist across browser restarts. Leith proposed adding a function to both Chrome and Firefox to disable this autocomplete function upon startup for those who have privacy concerns. He also has proposed to Apple that Safari’s default start page be reconfigured and an option to avoid unnecessary network connections. He has not heard back from any of the vendors on his suggestions.
So if you are a privacy-concerned user, what are your options? First, you should probably audit your browser extensions and get rid of ones that you don’t use or that have security issues, as Brian Krebs wrote recently. Second, if you feel like switching browsers, you could experiment with Brave or Authentic8’s Silo browser or Dooble. I reviewed two of them many years ago; here is a more updated review on some other alternative browsers done by the folks at ProtonMail.
If you want to stick with your current browser, you could depend on your laptop vendor’s privacy additions, such as what HP provides. However, those periodically crash and don’t deliver the best experience. I am not picking on HP, it is just what I currently use, and perhaps other vendors may have more reliable privacy add-ons. You could also run a VPN all the time to protect your IP address, but you will still have issues with the leaked backend collections. And if you are using a mobile device, there is Jumbo, which helps you assemble a better privacy profile. What Jumbo illustrates though is that privacy shouldn’t be this hard. You shouldn’t have to track down numerous menus scattered across your desktop or mobile device.
Sadly, we still have a lot of room to improve our browser privacy.
David, Two comments.
1. Why not Tor, as it is released?
2. Chrome tracking is more insidious and comical at the same time. Recently my wife began browsing for various ladies garments. And now I get ads for ladies garments. Why? I suspect it is because Chrome also associates the ad types with the originating IP address. Because Chrome and Google serve me well for finding all manner of tech info and quickly, I am less concerned about what they track about me. Also, I have long been immune to impulse buying and other ad techniques that work well on the majority.