When IT professionals talk about phishing attacks, they are quick to blame uneducated users who aren’t really focused on processing their emails. But while this is certainly one of the causes – and one of the reasons why phishing remains so popular among attackers – you can’t fault even the most eagle-eyed users from several things that are making it harder to spot phony emails. A combination of more subtle attacks using non-Roman URL characters, more focus on mobile man-in-the-middle exploits, greater use of SSL certificates and more mobile email usage have created new opportunities for phishers.
Homograph attacks. Even if you are the sharpest-eyed observer, you will have a hard time detecting this latest phishing technique that goes by the name Punycode or an IDN homograph typosquatting attack. The idea is simple: back in the day, the Internet standards bodies expanded the ability to handle non-Roman alphabet characters for domains and URLs. The trouble is that many of these characters look very similar to the ordinary ones that you and I use in our Roman alphabet. Spammers purchased domains that looked just like the all-Roman letters, with one or two changes using some other character set. This post from Wordfence shows how subtle these homographs really are, making it almost impossible for anyone to detect. There is further discussion on this site about how phishers operate.
More mobile email usage. This is making it harder to see (and then vet) the URL bar when a browser session is opened on your phone. The mobile app designers want as much screen real estate as they can to show a web page and this means that the URL line is often hidden or quickly moves off the screen as you scroll down. Even if you wanted to pay attention, you probably don’t bother to scroll back up to see it. What is making things worse is that the criminals are making better copies of real web pages. The crooks are getting better at using the exact same HTML code that a bank or retailer uses for their web pages, which makes them harder to distinguish, even if they are viewed on a full-sized PC screen.
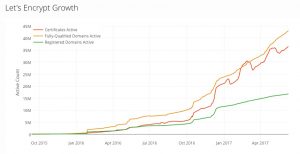 More SSL encryption usage. Ironically, an effort that began several years by Google and the non-profit foundation behind the Let’s Encrypt website have made problems worse. That website makes it dirt simple to obtain a free SSL certificate in a matter of seconds, so that warning signs in the URL bar of browsers when you aren’t connecting to a secure website are almost moot now. While it is great that more than half of all web traffic is now encrypted, we need better mechanisms that just a red/green indicator to help users understand what they are viewing.
More SSL encryption usage. Ironically, an effort that began several years by Google and the non-profit foundation behind the Let’s Encrypt website have made problems worse. That website makes it dirt simple to obtain a free SSL certificate in a matter of seconds, so that warning signs in the URL bar of browsers when you aren’t connecting to a secure website are almost moot now. While it is great that more than half of all web traffic is now encrypted, we need better mechanisms that just a red/green indicator to help users understand what they are viewing.
More frequent MITM attacks on mobile apps. Security researcher Will Strafach gave a report earlier this year and demonstrated numerous IOS apps that were vulnerable to man-in-the-middle attacks. These allow attackers to intercept data as it is being passed from a device to a server. That grabbed a few headlines, but apparently wasn’t enough. In a more recent report, he has continued to track these apps and shows that many of them are still vulnerable.
So what is being done? The browser vendors are doing a better job at detecting the homograph URLs (if you are not running Chrome 59 or Firefox 53, please do upgrade now). Many network security vendors are fine-tuning their tools to better detect compromised emails, or track reputations of malware control sites, or use other techniques to try to neutralize the phishers. Some enterprises are deploying secure browsers, to limit the damage of a phished link.
Clearly, this will take a combination of approaches to fight this continued battle. Phishing is a war of attrition. All it takes is one less-attentive user and the game is on. And it requires constant vigilance — by all of us.