 The WannaCry ransomware worm that plagued many people last week is notable for two reasons: first, it is a worm, meaning it self-propagates. It also uses a special exploit that was first developed by the NSA and then stolen by hackers. It first began on Friday and quickly spread to parts of Europe and Asia, eventually infecting more than 200k computers across more than 100 different countries. It moved quickly, and the weekend saw many IT managers busy to try to protect their networks. One researcher called it a “Frankenstein’s monster of vulnerabilities.”
The WannaCry ransomware worm that plagued many people last week is notable for two reasons: first, it is a worm, meaning it self-propagates. It also uses a special exploit that was first developed by the NSA and then stolen by hackers. It first began on Friday and quickly spread to parts of Europe and Asia, eventually infecting more than 200k computers across more than 100 different countries. It moved quickly, and the weekend saw many IT managers busy to try to protect their networks. One researcher called it a “Frankenstein’s monster of vulnerabilities.”
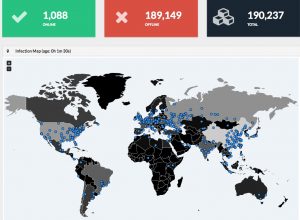
Most of the victims were using outdated Windows versions such as XP. This map shows real-time tracking of the infected systems, where the bulk of infections hit Russian sites, although Telefonia in Spain was also attacked.
The hardest-hit were numerous hospitals and clinics run by the British National Health Service. Apparently, they had an opportunity to update their systems two years ago but didn’t due to budgets. So far, the best analysis is on The Register.
WannaCry attack summary and timeline
American sites weren’t infected due to an interesting series of events. A young British security researcher who goes by the Twitter handle MalwareTechBlog discovered by accident a kill switch that stopped its operation. His account of that fortunate happenstance can be foundhere. Basically, by reverse engineering its code, he found that the malware checks for the existence of a specific domain name (which didn’t exist at the time and which he quickly registered). Once that domain had an operating “sinkhole” website, the malware attacks ended, at least until new variations are created without the kill switch or that check for a different site location. Sadly, the researcher was outed by the British tabloids. No good deed goes unpunished.
The story on payouts
One curious story about WannaCry is the small ransom payouts to date. About 100 people have been recorded paying any ransom, according to the three Bitcoin accounts that were used by criminals. (Yes, Virginia, Bitcoin may be anonymous but you can still track the deposits.) Other Bitcoim addresses could be used, of course, but it is curious that for something so virulent, so little has been paid to date.
Microsoft reaction and mitigation
The malware leverages an exploit that had been previously patched in mid-March by Microsoft and assigned the designation MS17-010. The company and took the unusual step to provide patches for all currently supported Windows along with Windows XP, Windows 8 and Windows Server 2003 versions.
Microsoft also recommends disabling SMBv1 and firewalling SMB ports 139 and 445 from the outside Internet. If you haven’t been doing these things, you have a lot of other problems besides WannaCry.
Microsoft’s president posted an op/ed blog piece saying “this attack demonstrates the degree to which cybersecurity has become a shared responsibility between tech companies and customers. The fact that so many computers remained vulnerable two months after the release of a patch illustrates this aspect. Users are fighting the problems of the present with tools from the past.” Speaking of the past, they didn’t mention how many people are still running ancient versions of Windows such as XP, but at least should be commended for having patches for these older systems.
Numerous security vendors have posted updates to their endpoint and network protection tools that will catch WannaCry, or at least the last known variant of it. And that is the issue: the hackers are good at morphing malware into something new that can pass by the defensive blocks. One interesting tool is this Python script that will detect and remove DoublePulsarexploits. That was the original NSA hack that can creates a backdoor to your system. In the meantime, as I said last week, hope is not a strategy.
You say that XP is outdated, but I believe that is only true in the sense that Microsoft is no longer issuing updates for it – even if they did publish a patch for this particular problem.
As far as developers of commercial systems are concerned, I believe XP did everything that was needed for the vast majority of applications. I don’t believe that systems ranging from ATMs to Medical instruments could gain anything from later systems – and they generally require greater resources just to run. It was also the best available operating system for over 8 years – longer than any other Microsoft OS. (Vista being a disaster which very many users never moved to) It also became available at a time when many new systems were being developed (just after the rush of changes at the turn of the century)
In many cases systems required certification before they could be used, and any change in OS would require some expensive re-certification – for no apparent benefit, especially in the medical instrument field.
This is not to say that I approve of critical systems continuing to use XP, but simply that I see the reasons for it. I also see that people are now much more skeptical about any new OS, and really want to wait for some time to see if it will stick. There really is a need for an OS which will be guaranteed to be updated forever and not have any backward compatibility issues.
If only Microsoft did not have the best software development environment …….. !
I agree with you Robert. XP was a wonder to behold, and did the job. But in the embedded space, those systems are a real source of threats today, and so we have to find an alternative, whether that be ChromeOS or Win10 or whatever. Thanks for your note.