Note: Since I wrote this story back in 2014, events have changed. Norse’s database and methods have been questioned, and the company has seen a massive staff layoff, including its CEO. I would be careful if you choose their products for now.
We all know it is an arms race on the Internet trying to protect our networks against bad actors. There are fake anti-virus alerts that masquerade as malware and an entire category of badness called ransomware that holds your hard disk hostage until you pay someone to unlock its hold on your data. And then there are traditional methods, such as what was used at Target and elsewhere to use legitimate credentials of people with wide-ranging network access to do their mischief.
It is all rather depressing. But because it is an arms race, the good guys have a few tricks up their sleeves too. The latest line of defense is to track sources of potential infections, down to geo-locating them in the physical world to the extent possible. This is what Norse Corp. offers its clients, and having seen some samples, I have to admit it is a great idea.
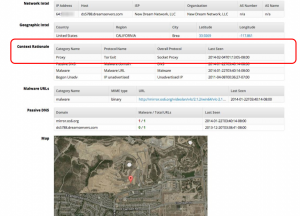 Here is a screenshot showing you what they capture. The idea is to instrument the vast unwashed Internet (TOR routers, peer-to-peer torrents, and other effluvia that runs across what all of us would not like to think about when we are trying to trying to Get Real Work Done). Norse has placed thousands of its capture appliances around the world and collected a database of more than 120 million malicious URLs. While that sounds like a lot, it isn’t when you compare this to the number of infected PCs or those on existing botnets. But what is significant is that they can find malware sources in the developmental stages, before they start infecting other computers.
Here is a screenshot showing you what they capture. The idea is to instrument the vast unwashed Internet (TOR routers, peer-to-peer torrents, and other effluvia that runs across what all of us would not like to think about when we are trying to trying to Get Real Work Done). Norse has placed thousands of its capture appliances around the world and collected a database of more than 120 million malicious URLs. While that sounds like a lot, it isn’t when you compare this to the number of infected PCs or those on existing botnets. But what is significant is that they can find malware sources in the developmental stages, before they start infecting other computers.
Of course, they aren’t the only ones with these appliances: Cisco, McAfee, BlueCoat, Bit9, Palo Alto Networks, and others have instrumented their customers’ routers and firewalls to capture similar information. Some of these companies score the source addresses and have integrated this reputation analysis into their firewall rules engines too. But to my knowledge, Norse is the only one that can locate these TOR exit nodes and start to identify what other IP addresses are being carried through them. And guess what? If you have to use TOR to hide your traffic, you probably aren’t sending nursery rhymes across the Interwebs. And because everything they observe is tied back to a common database, they can figure out some pretty important things. For example, when a hospital’s kidney dialysis machine is collecting credit card information or worse yet, doing actual payment transactions, that should send up a red flag.
I have written about this before, including most recently this piece in Information Security Magazine this past month. Too bad Target and Marriott and others didn’t have this technology when their insider accounts had been compromised. Yeah, too bad.
David,
Thank you for the email and response.
I agree that TOR, Onion Routing, Ultra Surf, Geolocation, and etc. are now addition yet another dimensions. The irony is ALL of these are old methods and now be revised. Barrier1 has ALWAYS had GeoLocation down to the CO switch of a community. We have a lot of examples where the big players could not. TOR and Onion routing is visible and they have specific attributes. Barrier1 identifies those attributes and either accepts or blocks. In addition, Barrier1 LEARNS from it. Ultra Surf represented both the masking and mutating abilities.
Barrier1 is the only Intelligent Threat Mgmt. system in Real Time that will identify TOR, Onion Routing, Ultra Surf, Polymorphic Attacks in real time.
Jim Libersky
Barrier1
763-230-1041
Much of the malware depends on infecting PC’s. You need not worry about that when you are using a Cirrus virtual desktop. The OS is Ubuntu, and all the apps you need are available .. LibreOffice, Firefox, Evolution, vtiger..
Thanks
Rick
The bad guys have some real advantages:
(1) Security is often beaten before it can be retooled to prevent that type of attack.
(2) People are lazy, inefficient, and feel safe, even when they aren’t (how many regularly speed or text while driving)? Even pros make configuration errors. The more complicated the system and overworked, undertrained, or unfocused the support, the more likely you will have a breach.
(3) People have a poor understanding of risk (95% of those surveyed considered themselves above average drivers or if it hasn’t happened to me, yet, it won’t happen). Those who have the religion have been burned before.
(4) Computer based attacks can be extremely ineffective, yet successful. A 0.001% infection rate worldwide is a LOT of computers.
(5) Security is *very important* until you actually have to do something or pay for it.
(6) Security measures are very visible and can often be tested prior to an actual attack.
(7) PICNIC errors are never soluble (Problem In Chair, Not in Computer). People will do things they aren’t supposed to and compromise security. Social engineering works *very* well.
(8) There is no magic security pill, as much as some people would like to believe there is.
(9) Security is rarely thought of as a normal business function. It is often an add-on or afterthought. It is quite natural. Even programmers do it. First they want to get it to work. Then, “What do you mean it can be exploited?”
(10) There is a LOT of money and advantage in crime and espionage. If it wasn’t worthwhile, no one would do it. Estimates put the monetary values of breaches, compromises, etc, and 100-200x what is spent on security software.
The real paranoid security people consider that they have already been compromised and don’t know it (yet). So they want to look for it. I often thought it wouldn’t be a big deal if you let everyone in, as long as you let no one out…. Security should be more symmetric. We need to be looking at what flows out, as well as what flows in. Those who are inside, as well as those who are outside. We worry more about the outside attacker. Big deal. In almost all cases, he turns an outside attack into an inside one. We worry about the malware and intruders coming from outside. Well, they aren’t a problem unless they can compromise something on the inside.
As the world becomes more mobile and the inside/outside line disappears, we need to hope that we can make every system and every network a secure tropical isle surrounded by an ocean full of sharks.