When we get emails from our CEO or other corporate officers, many of us don’t closely scrutinize their contents. Phishers count on this for their exploits. The messages often come around quitting time, so there is some sense of urgency so we will act before thinking through the consequences.
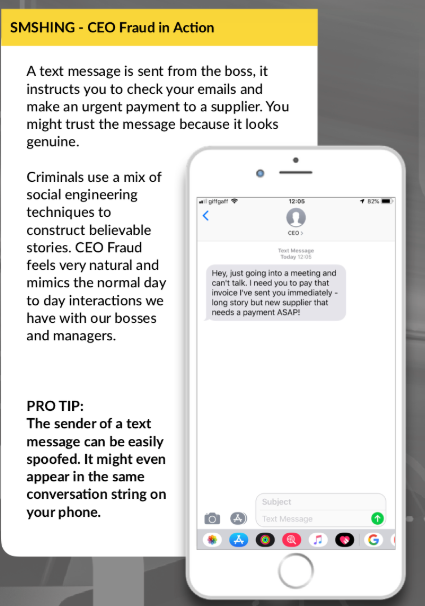
Here is an example of a series of emails between “the boss” (in reality, the phisher) and his subordinate that happened in November 2017. You can see the growing sense of urgency to make a funds transfer happen, which is the phisher’s stock in trade. According to FBI statistics, this type of fraud is now a $12 billion scam. And yes, the money was actually sent to this attacker.
KnowBe4, which sells phishing training services, categorizes the scam into two separate actions:
- First is the phishing attempt itself. It is usually called spear phishing, meaning that the attacker has studied the corporate organization chart and targeted specific individuals. The attacker has also examined who has fiduciary responsibility to perform the actual funds transfer, because at the heart of this scam it is all about the money that they can steal from your business.
- Next is all about social engineering. The attacker has to appear to be convincing and act like the boss. Often, the targeted employee is tricked into divulging confidential information, such as bank accounts or passwords. Many times they use social media sources to amplify their message and make it seem more legit.
The blog post mentions several different situations that are common with this type of fraud:
- Business working with a foreign supplier.
- Business receiving or initiating a wire transfer request.
- Business contacts receiving fraudulent correspondence.
- Executive and attorney impersonations.
- Confidential data theft.
 A new blog post by Richard DeVere here provides some good suggestions on how to be more vigilant and skeptical with these emails.
A new blog post by Richard DeVere here provides some good suggestions on how to be more vigilant and skeptical with these emails.
- Examine the tone and phrasing of the email. One time a very brusque CEO — who was known for this style — supposedly sent a very polite email. The recipient flagged it as a potential phish because of this difference.
- Have shared authority on money transfers. Two heads are better than one.
- As Reagan has said, trust but verify. Ask your boss (perhaps by calling directly) if this email really originated from him or her before acting on it. Phone calls and texts can be spoofed from your boss’ number. As the illustration above shows, this is quite common. Take a moment to process what is being asked of you.
- Report the scammer to the right authorities inside and outside your company.
The bottom line: be wary and take a breath when you get one of these emails.
Pingback: HPE blog: CISO faces breach on first day on the job | Web Informant