Earlier this summer, I wrote about how the world of SSL certificates is changing as they become easier to obtain and more frequently used. They are back in the news more recently with Google’s decision to add 45 top-level domains to a special online document called the HTTPS Strict Transport Security (HSTS) preload list. The action by Google adds all of its top level domains, including .Google and .Eat, so that all hosts using that domain suffix will be secure by default. Google has led by example in this arena, and today Facebook, Twitter, PayPal and many other web properties have supported the HSTS effort.
The HSTS preload list consists of hosts that automatically enforce secure HTTP connections by every visiting browser. If a user types in a URL with just HTTP, this is first changed to HTTPS before the request is sent. The idea is to prevent man-in-the-middle, cookie hijacking and scripting attacks that will intercept web content, as well as prevent malformed certificates from gaining access to the web traffic.
The preload list mitigates against a very narrowly defined attack that could happen if someone were to intercept your traffic at the very first connection to your website and decode your HTTP header metadata. It isn’t a likely scenario, but that is why there is this list. “Not having HSTS is like putting a nice big padlock on the front door of your website, but accidentally leaving a window unlocked. There’s still a way to get in, you just have to be a little more sophisticated to find it,” says Patrick Nohe of the SSL Store in a recent blog post.
This means if you thought you were good with setting a permanent 301 redirect from HTTP to HTTPS, you aren’t completely protected.
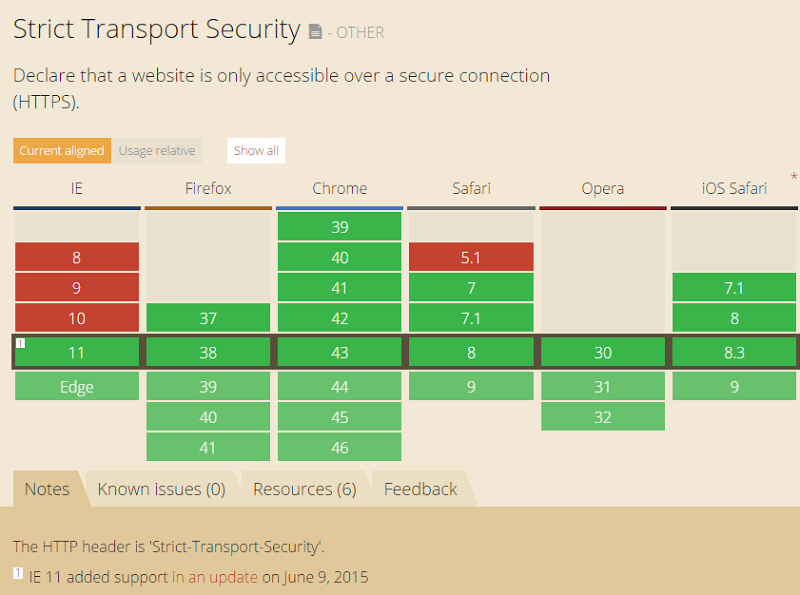
The preload site maintains a chart showing you which browser versions support HSTS, as shown above. As you might imagine, some of the older browsers, such as Safari 5.1 and earlier IE versions, don’t support it at all.
So, what should you do to protect your own websites? First, if you understand SSL certificates, all you might need is a quick lesson in how HSTS is implemented, and OWASP has this nice short “cheat sheet” here. If you haven’t gotten started with any SSL certs, now is the time to dive into that process, and obtain a valid EV SSL cert. If you haven’t catalogued all your subdomains, this is also a good time to go off and do that.
Next, start the configuration process on your webservers: locate the specific files (like the .htaccess file for Apache’s web servers) that you will need to update with the HSTS information. If you need more complete instructions, GlobalSign has a nice blog entry with a detailed checklist of items, and specific instructions for popular web servers.
After you have reviewed these documents, add your sites to the preload site. Finally, if you need more in-depth discussion, Troy Hunt has this post that goes into plenty of specifics. Healso warns you when to implement the preload feature: when you are absolutely, positively sure that have rooted out all of your plain HTTP requests across your website and never plan to go back to those innocent days.