 If you are ultra paranoid, what could be better than hiding your network traffic in such a way that no one could possibly intercept it? This is what Unisys is offering with its new Stealth appliance, which could make man-in-the-middle attacks and keylogger exploits obsolete, or at least more difficult to mount.
If you are ultra paranoid, what could be better than hiding your network traffic in such a way that no one could possibly intercept it? This is what Unisys is offering with its new Stealth appliance, which could make man-in-the-middle attacks and keylogger exploits obsolete, or at least more difficult to mount.
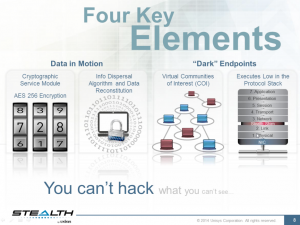
Stealth uses four layers of security (see diagram): each packet is encrypted with AES256, then split into three separate pieces and dispersed across the network, destined for a particular group of users that have to be running its protocols. Stealth has been around since 2005, and you can read my review of Stealth for Network World here.